Ever wondered can the most reliable and safe biometric security measures like fingerprints be bypassed? Well, let’s try to explore the answer.
People mostly rely on biometric security in comparison to traditional PINs or passwords for their device’s security. Among biometrics, fingerprint security is regarded as the most secure and convenient method of protecting smartphones as it can’t be easily duplicated or bypassed. However, Tencent Labs and Zhejiang University recently conducted research. In this research, they revealed a new attack which they called the “BrutePrint Attack”.
This attack exploits vulnerabilities in smartphones. These vulnerabilities enable hackers and even law enforcement to bypass your biometric security measures. In this article, we will explore the BrutePrint attack, how it works, and its implications. We’ll also see how hackers and law enforcement can hack your biometric security using this attack.
How BrutePrint Works?
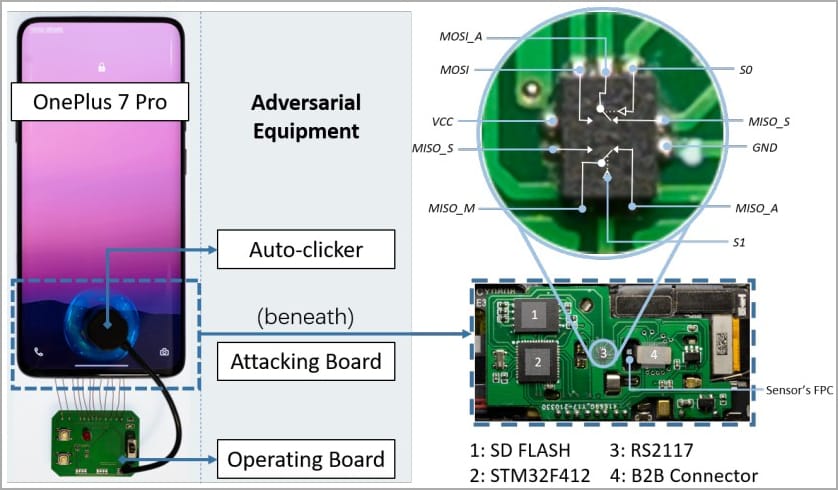
The BrutePrint attack is conducted by submitting an unlimited number of fingerprint images to the target device. These submissions are continued until a user-defined fingerprint is successfully matched. For a BrutePrint attack, the attacker needs physical access to the target device. The fingerprint database is required which can be obtained from sources like academic datasets or biometric data leaks. Specific equipment is also required for this attack.
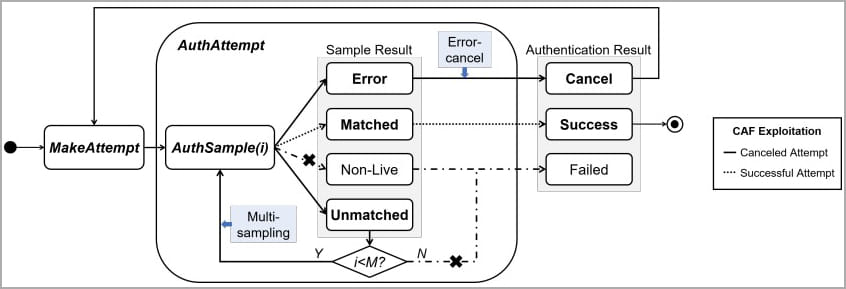
Unlike password-cracking methods, fingerprint matching relies on a reference threshold rather than a specific value. This means attackers can manipulate the False Acceptance Rate (FAR). FAR increase the acceptance threshold and facilitates easier creation of matches. BrutePrint works between the fingerprint sensor of the device and the Trusted Execution Environment (TEE), This advantages the attacker to utilize CAMF flaw to manipulate the mechanisms like multi-sampling and error-canceling mechanisms. There Terms are explained in detail below.
iOS devices exhibit stronger authentication security. It makes it difficult for attackers to brute-force an iOS device. Although the vulnerabilities like CAMF were discovered in certain iPhone models
Types of BrutePrint Attacks
Chinese researchers discovered two zero-day vulnerabilities, called Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL). These allowed researchers to overcome existing safeguards against brute-force attacks.
CAFM Attack
CAMF exploits multi-sampling and error-canceling mechanisms. It works by injecting a checksum error that terminates the authentication process before completion. It enables hackers to submit unlimited fingerprints without the system registering failed attempts.
MAL Attack
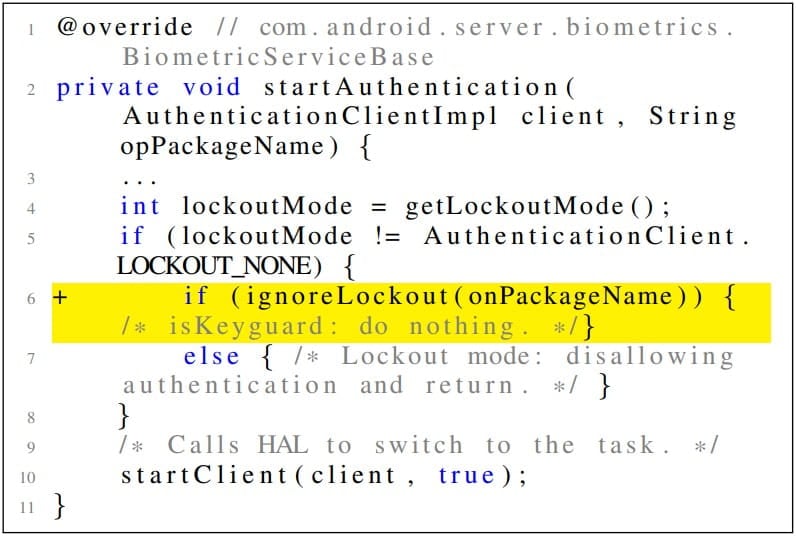
Meanwhile, MAL bypasses the lockout mode. Lockout mode is usually activated after a user consecutively makes failed unlock attempts. Attackers infer authentication results even when the device is in lockout mode using MAL Attack.
MITM Attack
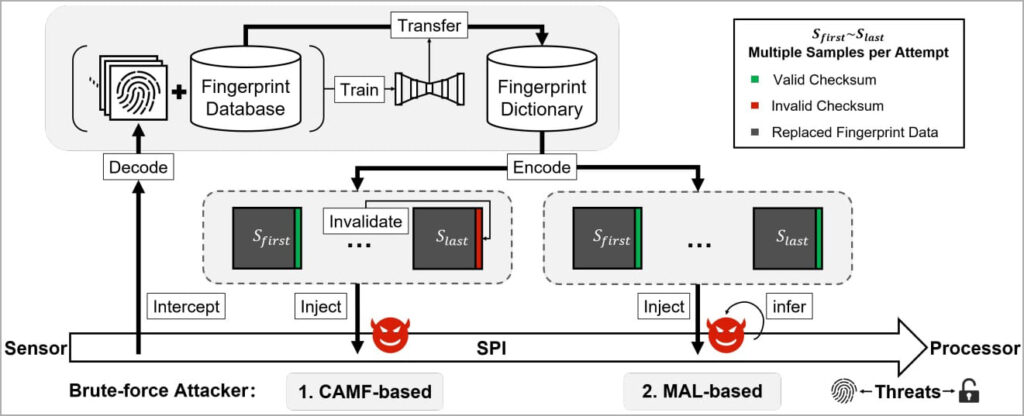
In addition to these vulnerabilities, the researchers found that the biometric data on fingerprint sensors’ Serial Peripheral Interface (SPI) were lacking proper safeguarding. Which was easy enough to expose the devices to a man-in-the-middle (MITM) attack.
A MITM attack is a cyber-attack where attackers position themselves between the sender and the receiver and spy on the communication between the two. They may also capture the transmitted fingerprint images. Once the attackers access these images, they gain the ability to manipulate or misuse the biometric data. This can lead them to bypass fingerprint-based authentication systems.
Android Vs iOS Security
The experiments performed by researchers further revealed some information like Android devices are particularly vulnerable to BrutePrint attacks. In the case of Android, attackers can brute-force a user’s fingerprint relatively easily and gain access to the device given enough time.
However, iOS devices exhibit stronger authentication security. It makes it difficult for attackers to brute-force an iOS device. Although the vulnerabilities like CAMF were discovered in certain iPhone models, the authentication security in iOS successfully prevents brute-forcing attacks.
iOS on MITM Attack
In addition to that researchers also demonstrated the SPI MITM attack. This attack highlighted the potential risk of fingerprint images getting hijacked during the transmission. Android devices lack fingerprint data encryption on the SPI. This makes them easily vulnerable to interception. However, things are different in Apple devices. They have fingerprint data encryption on their SPI. This vulnerability in Android devices compromises the integrity of biometric information which can lead to unauthorized access to personal data.
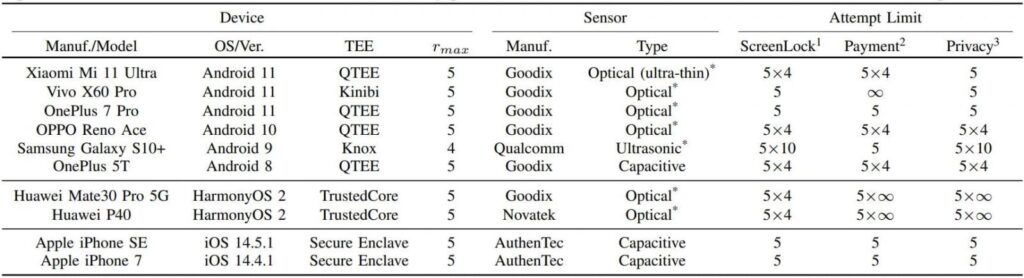
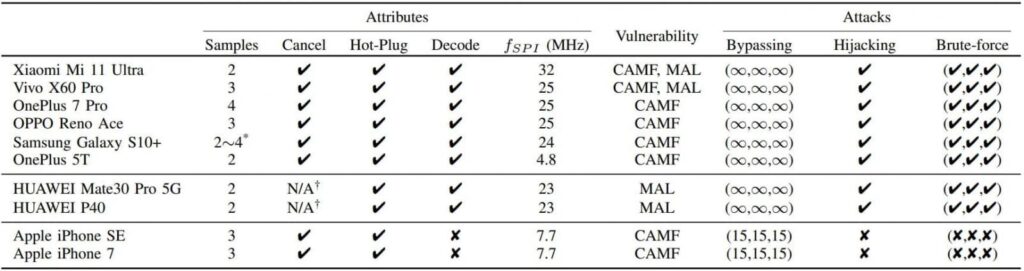
Tested Devices and Their Results
Researchers tested the vulnerabilities on 10 different Android and iOS Devices and found out all of them were vulnerable to at least one flaw. Here is the detailed chart of all the devices and the flaw they were vulnerable to.
The tested Android devices can allow unlimited attempts to unlock the device using different fingerprints. It makes the brute-force attack practically possible to unlock the device in a given enough time.
On the other hand, iOS possesses much stronger security measures for authentication which effectively prevents brute-force attacks.
The researchers however revealed that iPhone SE and iPhone 7 are vulnerable to CAMF. But they can only increase the number of fingerprint attempts to 15, which makes brute-forcing the owner’s fingerprint practically impossible.
All tested Android devices were found to be vulnerable to SPI MITM attacks. While iPhones remained resistant to the same attack.
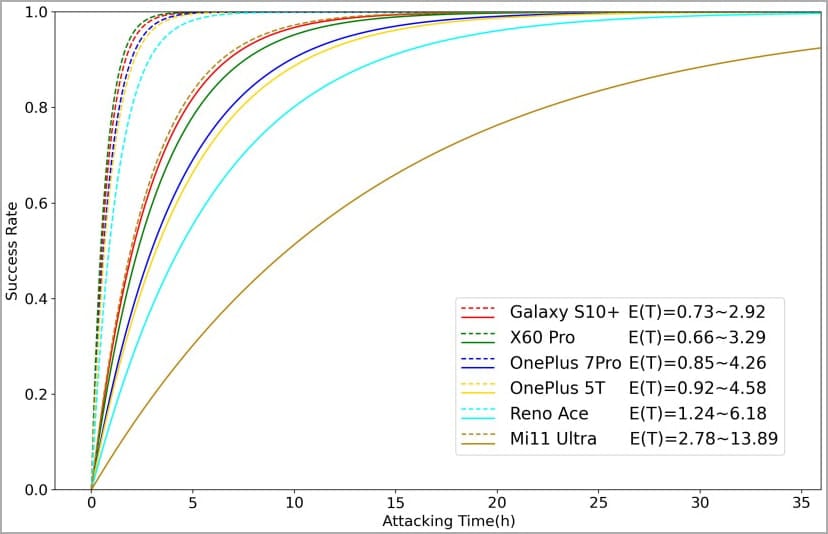
Required Time for a BrutePrint Attack
The performed experiments revealed that the required time for a successful BrutePrint attack on vulnerable devices ranges from 2.9 to 13.9 hours with a single enrolled fingerprint. However, with multiple fingerprints, the time dropped significantly to only 0.66 to 2.78 hours. This is due to the potential likelihood of generating matching fingerprint images. Here is a demonstration of time graph required to Bruteprint a vulnerable device.
Ethical and Legal Concerns
The BrutePrint attack can not only raise concerns about personal privacy but it also puts a question mark on ethical and legal implications. The criminals may use these methods to unlock the stolen devices, accessing valuable and private data.
On the other hand, the involvement of law enforcement agencies can use these techniques to bypass device security which raises serious questions about privacy rights and the ethics surrounding investigations. In certain jurisdictions, these actions can be considered a violation of basic rights. It can weaken the safety of individuals living in certain countries. The Governments of some countries are also considering banning End-to-end encryption. However, coming back, maintaining a balance between law enforcement needs and the protection of individual privacy rights is a complex challenge that must be addressed.
Implications and Risks
The research introducing the BrutePrint attack raised significant security concerns among biometric authentication users. Although the attack requires physical access to the target device, it is a serious question mark to user privacy and device security. An attacker can equip the inexpensive tools maybe by accessing academic datasets or biometric data leaks. Unlimited fingerprint attempts can then be made match is found.
Safety Measures
As technology continues to advance, researchers, manufacturers, and policymakers should work collaboratively to address emerging security risks like this. Few testing methods can be used to make sure that such issues are addressed just with their emergence. These methods include robust testing and evaluation of biometric systems, ongoing research into potential vulnerabilities, and the development of stronger encryption and authentication.
What Companies and Software Developers Can Do?
Furthermore, smartphone manufacturing companies and software developers must take this issue into consideration and take immediate action to lessen the associated risks. The identified vulnerabilities, such as CAMF and MAL must be addressed to avoid such exploitation of private biometric data. Software updates and patches can be rolled out for older devices. Furthermore, a few essential steps like implementing stricter limits on the number of fingerprint attempts, improving liveness detection, and enhancing encryption methods can be taken to ensure user privacy.
What Users can Do?
From the user’s end, proactive measures should be taken to protect personal and private information. Users must consider installing software updates regularly to ensure the latest security patches. Setting up a strong alphanumeric password alongside biometric authentication can prove to be an extra layer of security.
Conclusion
In conclusion, the discovery of the BrutePrint attack served as a stark reminder that biometric security measures like fingerprint locks are not foolproof and they can too, be exploited by hackers. The use of biometric information by law enforcement is also being questioned. The vulnerabilities identified by the researchers make continuous improvement and innovation in biometric security crucial. By taking necessary security measures like updating software regularly, and bringing up a responsible approach to the ethical use of biometric data, we can successfully create a safer digital landscape for all users.










Add comment