Internet keeps evolving just like laws applicable to it and its use. It has now become a hub where people can interact with each other anonymously, giving them the freedom to create and sustain communities. The former line is how a regular person would define the Internet, but that’s not how a Dark web user would describe it. This article will give a quick explanation of what is the dark web, what all happens on the dark web and how to access the notorious dark web.
What is Dark Web
Internet used by regular people is referred to as ‘Clearnet‘ because of its low encryption and hence less anonymity. Encryption has improved greatly on clearnet over the past few years keeping in view user privacy, but clearnet still allows service providers, governments and other entities to get a snoop of what we are trying to do or who might be using the service.

The darknet requires special configurations and networks such as Tor or I2P, while there are other ecosystems which offer better anonymity and greater features with lesser efforts, one such tool is known as Utopia P2P Ecosystem (guide). These provide enough security that guarantees anonymity. This anonymity grants everyone a superpower they fantasize, which is being invisible or a ghost where you can affect others but can not be held accountable for.
Dark Web CleanCoin crypto mixer Service description : When you use CleanCoin to mix your Bitcoins, you will receive Bitcoins that originate from lots and lots of different transactions and wallet addresses, making it almost impossible for someone to track your wallet activity.
Tor architecture provides two services – anonymous browsing, and hosting of anonymous services through the so-called ‘Tor Browser’. Although distinct, both services employ roughly the same protocols and rely on the same distributed infrastructure.
Deep Web vs Dark Web
Before we move further down with the article, let us first get one thing sorted out: Is Dark Web and Deep Web same ? and the answer is NO.
Deep web has no relation to dark web. Anything not indexed or not available for direct access i.e. requires to sign-in, make an account or pay a fee is categorized as deep web. Deep web content can be on clearnet, while dark web is not hosted on clearnet. Deep web also includes any content that its owners have blocked from web crawlers for indexing.
We are a team of 3 contract killers working in the US (+Canada) and in the EU. Once you made a “purchase” we will reply to you within 1-2 days, contract will be completed within 1-3 weeks depending on target. Only rules: no children under 16 and no top 10 politicians
Several websites supposedly offered assassinations for a hefty fee. There are many scams for such “Killer for Hire” aswell, where the kill doesn’t happen and at times the one hiring is blackmailed with the conversation.
What Is Offered On Dark Web
One might wonder what is dark web used for and mostly it is used for notorious purposes. However, that does not make the majority of its use, browsing is overwhelmingly more popular than hosting. Most Tor users have never visited any hidden website at a *.onion address; hidden services account for around 3–6% of overall Tor traffic. Most users instead use the software merely to browse the internet’s conventional address space more securely or anonymously. When we explore the limited percentage of traffic which is hosting websites, majority will be left surprised as to what all kind of stores are available.
| Category | Details |
|---|---|
| Arms | Trading of firearms and weapons |
| Drugs | Trade of illegal drugs, including illegally obtained prescription medicine |
| Extremism | Extremist ideologies, militant how-to guides and extremist community forums |
| Finance | Money laundering, counterfeit bills, stolen credit cards or accounts |
| Hacking | Hackers for hire, trade or distribution of malware or DDoS45 capabilities |
| Illegitimate pornography | Pornographic material involving children, violence, animals or materials |
| Nexus | Websites focused on linking to other illicit websites within the darknet |
| Other illicit | Materials that did not easily fit into the other categories but remain problematic |
| Social | Communities for sharing illicit material in the form of forums and social networks |
| Violence | Hitmen for hire, and instructional material on conducting violent attacks |
| Other | Non-illicit content, political content, drop sites, info reps, legitimate services |
| None | Websites which were completely inaccessible |
Categorization of Web-based onion services will help you understand what this power has curated with Drug related trades making upto 15.4% of the Dark web.
| Category | Percentage |
|---|---|
| Gambling | 0.4 |
| Guns | 1.4 |
| Chat | 2.2 |
| New (not yet indexed) |
2.2 |
| Abuse | 2.2 |
| Books | 2.5 |
| Directory | 2.5 |
| Blog | 2.75 |
| Porn | 2.75 |
| Hosting | 3.5 |
| Hacking | 4.25 |
| Search | 4.25 |
| Anonymity | 4.5 |
| Forum | 4.75 |
| Counterfeit | 5.2 |
| Whistleblower | 5.2 |
| Wiki | 5.2 |
| 5.7 | |
| Bitcoin | 6.2 |
| Fraud | 9 |
| Market | 9 |
| Drugs | 15.4 |
What’s For Sale on Dark Web
Dark web is mostly known because of criminal activities and is frowned upon in society. However, it’s main aim is to give everyone the freedom they were promised and it is a haven for a lot of good people as well. As with everything the bad actors get more attention and that is the case with dark web aswell.
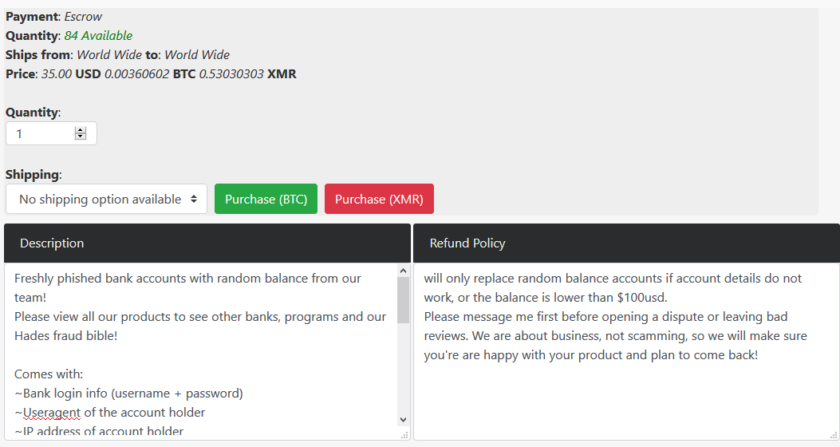

Our notes are made with the highest quality cotton fibre, all security features are included: watermarks, security thread, microprint, magnetic ink, color shifting ink, etc
A seller on dark web boasting about their product while highlighting their details.
Various products and services are being offered starting from $10 for a stolen credit card to a Identification card worth of $550.
| Category | Product | Avg. Price |
|---|---|---|
| Credit cards | Cloned Mastercard with PIN | $16 |
| Cloned VISA with PIN | $25 | |
| Credit card details and account balance up to $1000 | $12 | |
| Credit card details and account balance up to $5000 | $20 | |
| Walmart account with credit card attached | $10 | |
| PayPal | Stolen PayPal account details, minimum $100 | $198 |
| PayPal transfer from stolen account, $1000 – $3000 | $320 | |
| PayPal transfers from stolen account, $3000+ | $155 | |
| Fake documents | US driving license, average quality | $70 |
| US driving license, high quality | $550 | |
| Europe national ID card | $550 | |
| Social Media | Hacked Gmail account | $155 |
| Hacked Instagram account | $55 | |
| Hacked Facebook account | $75 | |
| Instagram followers x 1000 | $7 | |
| Instagram likes x 1000 | $6 | |
| TikTok followers x 1000 | $15 | |
| Twitter retweets x 1000 | $25 | |
| Twitch followers x 1000 | $6 | |
| DDoS Attacks | Insecure website, 10-50k requests per second, 1 hour | $10 |
| Unprotected website, 10-50k requests per second, 24 hours | $60 | |
| Unprotected website, 10-50k requests per second, 1 week | $400 |
How To Browse The Dark Web
All this activity, this vision of a bustling marketplace, might make you think that navigating the dark web is easy. It isn’t. The place is as messy and chaotic as you would expect when everyone is anonymous, and a substantial minority are out to scam others.
Accessing the dark web requires the use of an anonymizing browser called Tor. Procedure of Installing Tor is simple.
- Download Latest from the official Tor Project website
- Run the downloaded file and install
- Start browsing on Tor through the installed Tor Browser
Note: You may run Tor from the desktop shortcut but if you open it from the folder you installed it in then don’t be alarmed as it will be named firefox.exe. You can easily find it because of its onion icon as well.
You may be wondering what to open on Tor. Let’s list some sites which you can browse and make use of Tor.
- Grams – One of biggest Tor search engine but it returns results that are repetitive and often irrelevant to the query. Link lists like
- The Hidden Wiki – Lists sites available on Tor, while the list might return many 404’s.
- Facebook – Yes, Facebook is on Tor. The engineer who developed Facebook’s Tor branch pointed out that authentication in the Tor network is even better than on the more widely used internet protocols
- Dream Market – A Commerce Website
- WikiLeaks – Whistle Blower website
- Book Library – A collection of full-text books which are hard to find on clearnet
- New York Secure Drop – New York Secure drop website known as ‘Project Strongbox’
Conclusion
Hidden services increase privacy because there is no longer an exit node: both parties to the transaction are within the Tor network. Secondly, the protocol improves authentication, by making a so-called man-in-the-middle attack significantly more difficult. Facebook, for instance, at https://facebookcorewwwi.onion, is not just revealing the social network’s identity on the dark web; it is guaranteeing it while protecting the user. It does not mean that Facebook will not be able to collect data as it is their website the only thing Facebook will not be able to get is your actual IP address and location as those are not shared on Tor.
Proponents of hidden services argue that the cryptographic protocols that power the internet today were at the fringe of software development and considered a threat as late as 1995. Hidden services, they argue, are what ‘https’ was 20 years prior: the future of security, not a threat to security. These arguments are strong, and cannot be dismissed; the technology may well mature and move into the mainstream in the future.













Add comment