Drive-by downloads became increasingly common in 2008. With webmasters becoming more aware of security issues, the criminals out there are always looking for new techniques to ensure that their malware survives longer.
And what could be easier than to use Google? Everybody does – so why shouldn’t virus writers? Recently we’ve been seeing attacks which work in the following way.Â

The malware writers start by doing Google searches to identify popular websitesÂ
The most popular sites thrown up by each search are then ‘pen-tested’ for vulnerabilities. The most vulnerable websites are then compromised and in order to cover their tracks, malware writers aren’t adding code to these compromised pages in the form of new files or even obfuscated code. Instead, they’re simply modifying scripts that are already running on the compromised pages. In this particular case, the new parameters added to the existing script include the following function: (–referer=http://www.google.com/).
Â
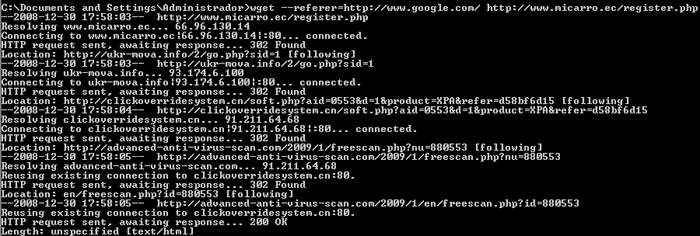

This function checks where the visitor to the infected page has come from. If it’s from a link in a Google search, then you automatically get re-directed to a series of malicious web sites – ones that have nothing to do with the original site. The result: an infected computer.
Â


Interestingly enough, the redirect doesn’t work if you simply type in the name of an infected website. None of the injected script functions will run – all you see is the page that you wanted. This helps prevent webmasters, employees and regular visitors to the site from suspecting infection, while the criminals still achieve their goals:
Â
- infecting numerous people
- hiding the malicious script from the webmaster to ensure a longer life for the malware.
So this type of attack doesn’t just harm users; it can also lead to innocuous websites getting blacklisted by security products.
Incidentally, it’s not just websites which have been optimized to achieve high search rankings that are being used; the criminals are also targeting some security sites. For instance, there’s been a lot of talk about fake antivirus solutions such as Antivirus XP. If you’re using Google to try and find information about this, the search results will come up with a lot of different pages – the only problem is, if you click through to a site from the Google results list, the modified script on the hacked security server will execute Antivirus 2010 on your machine.
Compromising websites optimized for search engine success and infecting users through a series of malicious re-directs is bound to be a popular attack vector in 2009 and will undoubtedly cause webmasters new headaches.
This case just goes to show that nothing on the Internet is as safe as it might seem. And it’s not just Google that’s affected – I tested this attack scenario using Yahoo! and MSN, and the results were the same. We detect the malware used in the case detailed above as Trojan-Downloader.Win32.Fraudload.vffa, and we’re bound to see more variants of it, so make sure you keep your antivirus software up to date!









For Hacking Tips and Tricks