Powered via Telegram bots and distributed through android applications, Android.spy.377.origin is a new Trojan Spyware, specifically targeting Iranian users to collect confidential data. Cyber-criminals remotely control the spyware by executing commands using message-exchange protocol of Telegram. Malicious programs are named Insta Plus, Profile Checker, and Cleaner Pro.
Telegram Vulnerability & Spyware Functions
As Telegram message exchange protocol provides simple method of communication, attacker does not need to enable port forwarding on victim’s device. However attacker first need to develop their own Bot, token generated by this Bot is embedded into Trojan’s configuration file. Once the victim device is infected, the attacker is able to control it through the automatically created channel.
After being launched, program offers user to check their profile rating among other telegram users. Victim is asked to provide their personal ID, Trojan then generates an arbitrary number of profile visitors without performing any real check.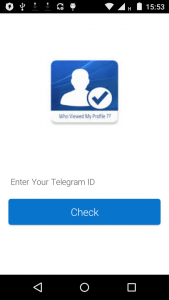

After this apparent legitimate function, program removes its shortcut from home screen, hides itself and start copying contact list, SMS, and Google account data in text files in the directory /Android/data/ .
• — contains information about contacts
• — contains information about all saved incoming and outgoing SMS
• — contains information about the user Google account
Besides this Trojan is also able to take photo with front camera, which along with other text files, is loaded to command and control server. Android.spy.377.origin then connects to Telegram bot, sends user’s information to bot and waits for further commands from spyware developers. It may receive following commands:
• call — make a phone call
• sendmsg — send an SMS
• getapps — forward information about the installed applications to the server
• getfiles — forward information about all the available files to the server
• getloc — forward device location information to the server
• upload — upload to the server the file that is indicated in a command and stored on the device
• removeA — delete from the device the file specified in a command
• removeB — delete a file group
• lstmsg — forward to the server the file containing information about all the sent and received SMS, including sender and recipient phone numbers, and message contents
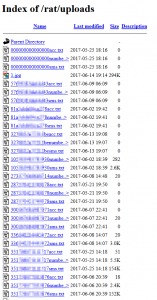

Trojan tracks SMS and alerts the developers’ Telegram bot whenever new message is sent or received or the device location is changed.
Unfortunately all Telegram users have now become official target of the newly created Android.spy.377.origin Trojan Attack despite the encrypted communication of the messenger. In order to protect their data, users should install applications developed and distributed only by authentic sources.













I know of one of the best hackers who I can vouch for. He is very good and reliable. he has helped me with so many issues with my my husband’s phone, because we had issues with cheating, he was cheating a lot and he helped me hack his phone and everything without him knowing and I was monitoring everything he was doing. Just contact him for any hacking related issues like hacking phones, computers, emails. Facebook accounts, WhatsApp, Instagram. Just mail him and you will get a good hacking service. Contact him on [email protected]