The emergence of Kamran spyware, targeting users of a regional news website, has raised concerns among cybersecurity experts.
Distributed through a possible watering-hole attack on the Hunza News website, the spyware prompts users to grant permissions, allowing access to sensitive data. With its unique code composition, attributing Kamran to a specific APT group is challenging.
This article explores Kamran’s operation, data exfiltration methods, and provides recommendations to mitigate the risk of falling victim to such attacks.
Key Takeaways
- Kamran is an Android spyware that specifically targets Urdu-speaking users in the Gilgit-Baltistan region of Pakistan.
- The spyware was distributed through a possible watering-hole attack on the Hunza News website.
- At least 20 mobile devices have been compromised by Kamran, which has a unique code composition that distinguishes it from other known spyware.
- The malicious app containing Kamran was available for download from the Hunza News website, and the developer certificate used to sign the app was issued on January 10, 2023.
Kamran Spyware: An Overview
The Kamran spyware can be summarized as a sophisticated Android malware targeting regional news website users. Specifically designed to target the Urdu-speaking community in the Gilgit-Baltistan region, Kamran has had a significant impact on its victims.
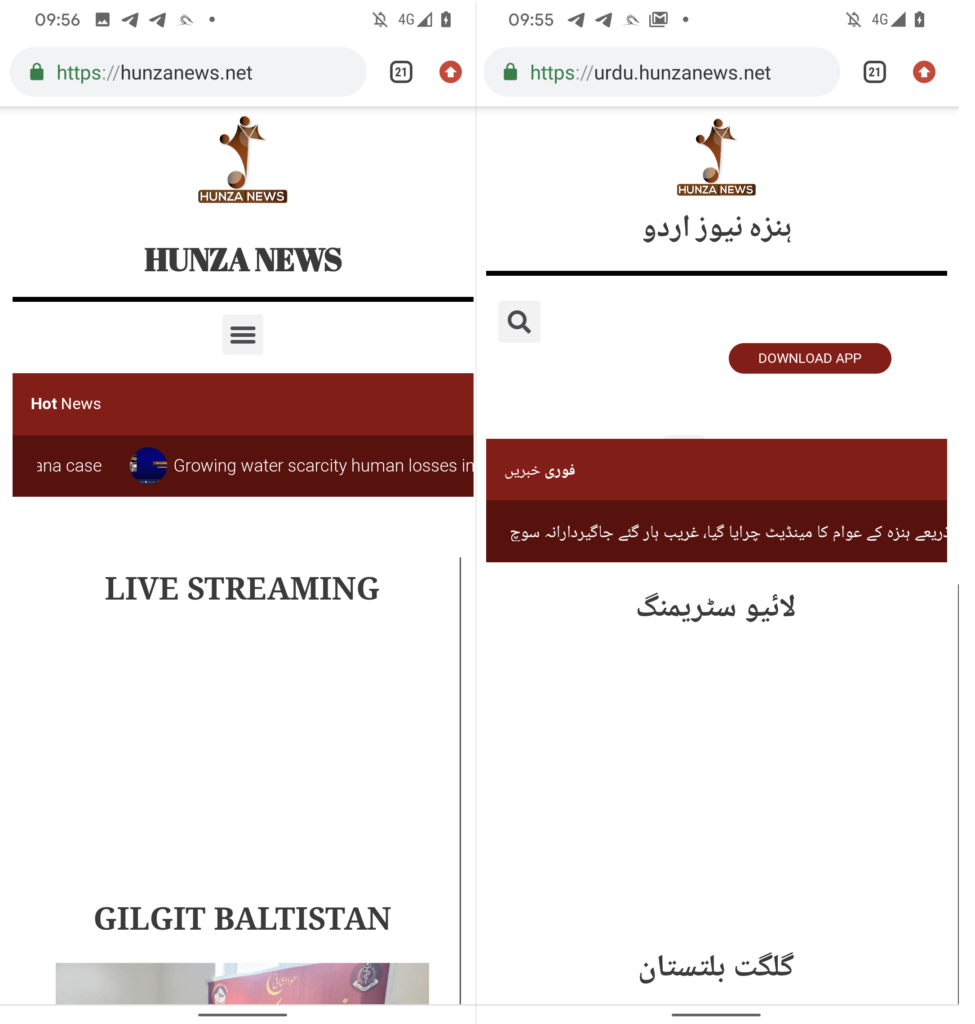
The spyware was distributed through a possible watering-hole attack on the Hunza News website, a popular online newspaper delivering news related to the region. The impact of Kamran on the Urdu-speaking community cannot be understated, as it compromises the security and privacy of their smartphones.
To prevent falling victim to Kamran, it is crucial for users to be vigilant and only download apps from trusted and official sources. Additionally, implementing strong security measures, such as regularly updating software and using reliable antivirus software, can help detect and prevent the infiltration of Kamran spyware.
Distribution Method and Targeted Users
Kamran spyware was distributed through a possible watering-hole attack on the Hunza News website, targeting Urdu-speaking users in the Gilgit-Baltistan region. This distribution method involves compromising a legitimate website of Hunza News frequented mostly by the local users of the area and injecting malicious code into it.
When the users visit the compromised website, they unknowingly download and install the Kamran spyware onto their Android devices. This method allows the attackers to reach a large number of users who trust the website and its content.
Malicious App Permissions and Data Access
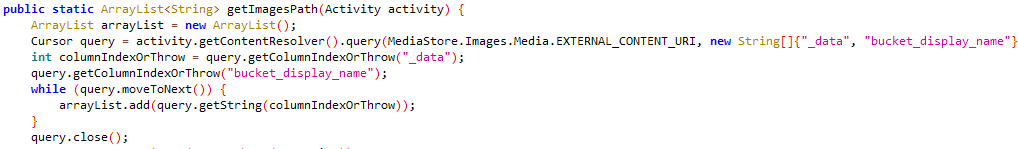
Users of the Kamran spyware are prompted to grant various permissions upon launching the malicious app. These permissions include access to sensitive data such as contacts, calendar events, call logs, location information, device files, SMS messages, and images.
Granting excessive app permissions can have serious implications for user privacy and security. By allowing the spyware to access such personal information, users are putting themselves at risk of identity theft, financial fraud, and unauthorized surveillance.
It is essential for users to be aware of the potential privacy concerns associated with granting these permissions and to exercise caution when installing apps from unknown sources. User awareness and education are crucial in protecting personal information and maintaining online security.
Gilgit-Baltistan: The Region at Risk
Gilgit-Baltistan faces a significant risk in relation to the Kamran spyware. The presence of this malicious software has several implications for regional security, including:
- Impact on regional security: The Kamran spyware poses a direct threat to the security of individuals and organizations in Gilgit-Baltistan. By infiltrating smartphones and collecting sensitive data, it compromises the privacy and confidentiality of users, potentially exposing them to further risks.
- Countermeasures against Kamran spyware: To mitigate the risk posed by the Kamran spyware, it is crucial to implement robust countermeasures. This includes raising awareness among users about the dangers of downloading apps from unknown sources and emphasizing the importance of only installing applications from trusted and official sources. Additionally, organizations should enhance their cybersecurity measures to detect and prevent such attacks.
Protecting the region from the Kamran spyware requires a comprehensive approach that addresses both individual and organizational aspects of cybersecurity.
Hunza News Website: The Potential Source of Attack
The potential source of attack in the case of the Kamran spyware targeting regional news website users is the Hunza News website. The website, which has been active for over 10 years and gained online readership, serves as a potential attack vector for the distribution of the Kamran malware.
The impact on regional news websites is significant, as the compromise of the Hunza News website allowed the malicious app containing the Kamran spyware to be available for download.
This highlights the importance of maintaining the security of news websites, as they can be exploited to target specific user groups. Regional news websites should take necessary measures to protect their platforms and users from potential attacks.
History of Hunza News Android App
The history of the Hunza News Android app dates back to 2015 when it was first introduced on the Google Play store. The app was initially launched with the aim of presenting website content in a user-friendly way. In the second half of 2022, the official app was taken down from the Google Play store, making it unavailable for download. However, since March 21, 2023, the Hunza News website reintroduced the option to download an Android app, exclusively visible on the Urdu language variant. This app became the source of the Kamran spyware, impacting the Urdu-speaking users of the Gilgit-Baltistan region. The availability of the Hunza News Android app provided an opportunity for the distribution of the Kamran spyware, affecting the security and privacy of its users. it is very important for companies to ensure that such applications are shared through official stores rather then directly listing the .apk’s .
Victimology: Who Is Affected by Kamran Spyware
Urdu-speaking residents of the Gilgit-Baltistan region are the primary targets of the Kamran spyware. The impacted demographics of the spyware are individuals who rely on the Hunza News website for news and information. These targeted users exhibit specific behavioural patterns, such as visiting the website regularly and accessing its content in Urdu.

Kamran spyware is distributed through a possible watering-hole attack, where the malware is injected into the website and downloaded by unsuspecting users. The spyware prompts users to grant various permissions upon launching, allowing it to access sensitive data on their devices. It collects information such as contacts, call logs, SMS messages, and images. This data is then uploaded to a command and control server which is being hosted on a firebase server.
The Kamran spyware attack has affected at least 22 compromised smartphones, with five located in Pakistan. The total amount can be higher while keeping in view the traffic received on the website.
Kamran’s Data Gathering Capabilities
Kamran spyware exhibits its data gathering capabilities through the prompt for various permissions upon launching the malicious app. While the spyware was not very advanced as it was only gathering data when the app was in focus.
When the app is opened, Kamran sends the collected data, along with any new data meeting its search criteria, to the command and control server. The data exfiltration techniques employed by Kamran involve repeatedly sending the same data to the server.
These activities raise serious implications for user privacy, as sensitive information can be accessed and potentially misused by malicious actors.
The malicious app appeared on the website sometime between January 7, 2023, and March 21, 2023; the developer certificate of the malicious app was issued on January 10, 2023. During that time, protests were being held in Gilgit-Baltistan for various reasons encompassing land rights, taxation concerns, prolonged power outages, and a decline in subsidized wheat provisions
Recommendations to Protect Against Kamran Spyware
To safeguard against the Kamran spyware, it is crucial to implement effective security measures and follow best practices for app download and usage. Here are some recommendations to protect against Kamran spyware:
- Install reliable anti-malware software: Use reputable security solutions that can detect and remove Kamran spyware. Regularly update the software to ensure it is equipped with the latest threat definitions.
- Be cautious when downloading apps: Only download apps from trusted and official sources such as Google Play Store. Avoid downloading apps from unknown sources or third-party app stores, as they may contain malware like Kamran.
- Practice good mobile device security: Enable app verification, which scans apps for potential threats before installation. Keep your operating system and apps up to date with the latest security patches. Avoid clicking on suspicious links or downloading attachments from unknown sources.
Conclusion
In conclusion, the emergence of Kamran spyware targeting users of a regional news website in the Gilgit-Baltistan region raises concerns among cybersecurity experts. The unique code composition of Kamran makes it challenging to attribute to a specific advanced persistent threat group.
It highlights the importance of downloading apps from trusted sources to mitigate the risk of falling victim to such attacks. Protecting sensitive data and being vigilant against potential threats is crucial in today’s digital landscape.










Add comment