The security of fingerprint-based authorizations has been the subject of heated debate for years. In 2013, shortly after the release of the iPhone 5S with TouchID, researchers showed that it was possible to deceive the technology by photographing a fingerprint left on a glass surface and using it to make a molding that could cheat the system. But technology is constantly advancing and its improvements have given reason for hope.
Last year, for example, manufacturers started equipping their smartphones with ultrasonic fingerprint scanners hidden under the screen, so that they would not need other panels and they would, at least in theory, be safer.
Security experts at Cisco Talos decided to see if it was easy to fool different types of fingerprint scanners from modern devices, or if the technology was finally secure.
The results were rather discouraging: the majority of smartphones and tablets were able to be duped in 80 to 90% of the cases and this success rate sometimes reached 100%
Fingerprint Authorization – The Theory
Let’s first recall how fingerprint scanners work. The basic principle is simple. Place your finger on the scanner of a smartphone or laptop, or even on a smart lock, and the sensor will extract an image from your fingerprint. Each type of scanner recognizes fingerprints in its own way. The Cisco Talos security team concentrated on the three most popular design
Capacitive Fingerprint Scanner
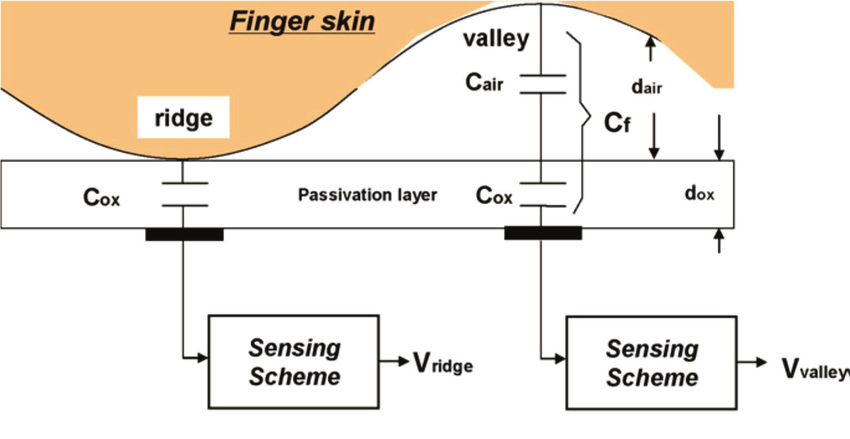

Capacitive scanners are the most common. They generate an image through a small electric charge generated by integrated miniature capacitors which can store electricity. When the finger touched the scanner, it discharges these capacitors. Greater contact (fingerprint bumps) causes greater discharge; the spaces between the skin and the sensing (the hollow of the fingerprints) cause a light discharge. The scanner measures the difference and identifies the pattern.
Optical Fingerprint Scanner
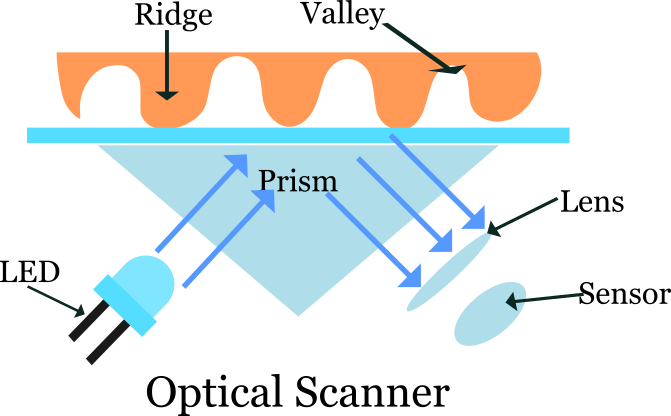

Optical scanners take a photo of the fingerprint. The device illuminates the finger through a prism, the bumps and hollows reflect this light differently and the sensor reads the information and converts it into an image.
Ultrasonic Fingerprint Scanner
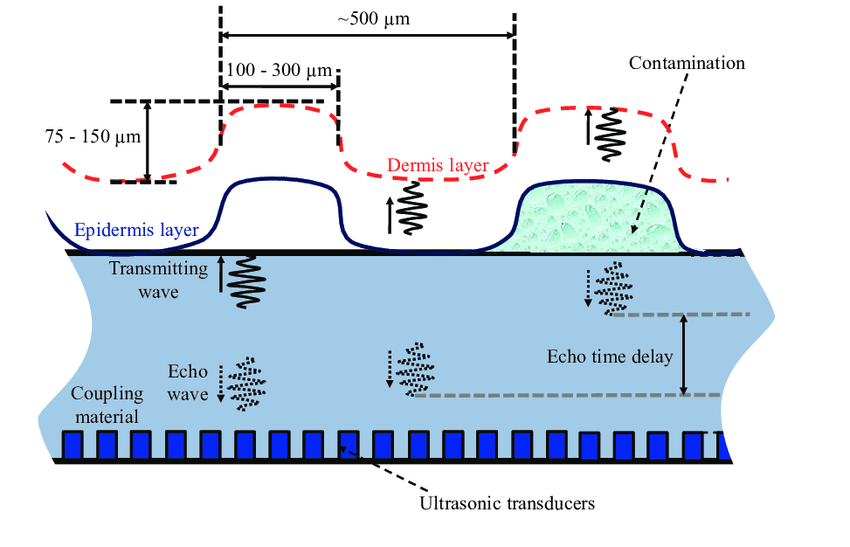

Ultrasound scanners use an ultrasonic signal instead of light and record the echo generated by bumps and dips (just as in the case of light reflection, bumps and dips have different echoes). This type of scanner does not need to be in contact with the finger and can, therefore, be placed under the screen. Also, it “hears” not only the part of the finger close to the surface but also the edges farther from the sensor, so that the image is closer to three-dimensional reality. This helps the scanner to detect fakes that use flat fingerprint copies.
Once your fingerprint has been obtained, the scanner or the operating system compares it to that saved in the device. Since no existing fingerprint reading method is perfect, each manufacturer allows a certain margin of error.
The higher the margin, the easier it is to falsify a fingerprint. If the settings are stricter and the margin of error is lower, the scanner is more difficult to deceive, but the machine may also fail to recognize its real owner.
How Researchers Falsified Fingerprints
To make a physical copy of a fingerprint, you have to acquire one. The research team found three ways to do this.
Method 1 : Molding Technique
It is possible to cast the fingerprint of the target when, for example, the victim is unconscious or unwell. Any soft material which hardens is suitable, for example, plasticine.


An attacker can then use the mold to make a false finger. The obvious difficulty is that the aggressor needs to have physical contact with the victim to be able to pull of this method of fingerprint spoofing.
Method 2 : Obtain a Scanned Image
Another technique is to obtain a fingerprint taken using a scanner. This method is more complicated from a technical point of view, but not all companies that handle biometric data store it reliably, much to the delight of thieves. So it’s not difficult to find scanned fingerprints online or buy them cheaply on the darknet.
Then the flat image must be transformed into a 3D model and printed with a 3D printer. First of all, the program in which the researchers created the design did not allow them to define its size. Then the photopolymer used by an economical 3D printer had to be heated after printing, which changed the dimensions of the model.
Third, when the researchers finally succeeded in making a correct model, it turned out that the polymer it was made of was too hard, and not a single scanner fell into the trap. As a backup, the researchers decided to print a molding, instead of a finger model, which they then used to make a finger prosthesis from a more elastic material.
Method 3 : Lift of Fingerprints from Surface
Another option and it is surely the simplest, is to photograph the fingerprint that the victim left on a glass surface. This is exactly what happened in the case of the iPhone 5S. The image is processed to obtain the required level of clarity, then, as before, pass is through a 3D printer.
As the researchers noted, the 3D printing experiments were long and tedious. They had to calibrate the printer and seek the correct size mold with hit and trial and the actual printing of each model (50 in total) with the needed settings lasted an hour. So making a fake fingerprint to unlock a stolen smartphone is not a quick job at all. Nor is copying the fingerprint of a sleeping victim a very quick method.
Making a mold to recreate the fingerprint is only half the task. The choice of material for the model itself turned out to be much more difficult since the false impression was intended to be tested on three types of sensors, each with a different method of reading fingerprints. For example, the fact that a material can conduct current is not important for ultrasonic and optical sensors but is essential for capacitive sensors.
However, this part of the process is accessible to everyone. The best material for false impressions is cheap textile glue.
Devices used for False Fingerprints
The researchers tested their copies on several smartphones, tablets and laptops from different manufacturers, as well as on a smart lock and two USB keys protected by a fingerprint sensor: Verbatim Fingerprint Secure and Lexar Jumpdrive Fingerprint F35.
The results were rather discouraging: the majority of smartphones and tablets were able to be duped in 80 to 90% of the cases and this success rate sometimes reached 100%. The molds printed in 3D were the least effective, but the difference was not significant; the three methods described above worked well.
There have been exceptions. For example, the research team was completely unable to crack the Samsung A70 smartphone (but it should be mentioned that the A70 is also most likely not to recognize its real owner).


Windows 10 devices have also proven to be impenetrable, regardless of the manufacturer. Researchers attribute this remarkable consistency to the fact that the operating system itself performs a fingerprint comparison: so little depends on the manufacturer of the device.
As for protected USB keys, they have proved worthy of the name, although they too could be exposed to a more sophisticated attack but they proved well in the various attacks described above.
Finally, the easiest to fool has been the ultrasonic fingerprint scanners. Despite their ability to perceive a 3D image, they are fooled by false prints if a real finger presses them against the sensor.
According to the researchers, the security of fingerprint-based authorizations leaves much to be desired, and to some extent, the situation has even deteriorated compared to previous years.
Conclusion
Making a fake finger is a fairly expensive process, at least for now, which means that the ordinary user doesn’t have to worry much. But it’s not the same if you’re in the cross hairs of a criminal group or a well-funded intelligence service. In this case, it is best to protect all your devices with a password. After all, cracking a strong password is harder and you can always change it if you think it may have fallen into the wrong hands.












Add comment