From this word onward avoid using a USB cable which is NOT owned by you. An ordinary looking USB Cable bearing all the markings of an official Apple charging cable or for an Android device might have an embedded Wifi module hidden , which will takeover your machine once you connect to it.
MG, The creator of Mr Self Destruct and Bad USB Cables came up with OMG Cable (Offensive MG Kit) where an ordinary looking USB cable is capable of connecting to a WiFi network and may compromise your machine. These attacks are known as HID (Human Interface Device) Attacks:
The HID attack is a scenario where an attacker takes a programmable embedded development platform and an associated software package and creates a USB device which when plugged into a computer will execute a pre-configured set of keystrokes to drop a malicious payload onto the target computer
Mr Self Destruct and Bad USB Cables , What ?
What is Mr Self Destruct
A USB device capable of injecting a payload , which can either be a keylogger or just be used to mess up your device before the USB device self destructs , yeah literally burns.


You could even have the Mission Impossible sort of self destructs if that is your thing , although that would not serve any purpose
Quick test of a new variant. This looks way better than I thought it would. pic.twitter.com/6Qnwh6EJan
— _MG_ (@_MG_) September 26, 2017
You can read about the whole Mr Self Destruct Project on authors official website.
What is a Bad USB Cable
MG’s obsession with USB devices and cables made him practice and learn more stuff and as he did that he shared his findings with the word. A Bad USB Cable is a simple USB cable with a malicious code embedded in it , while the cable still works as it is intended to work i.e. charge an iPhone or even an iMac. Once a Bad USB Cable is plugged in device it would execute the payload already programmed on it. Bond Stuff ? well Spy Cables are a thing of reality. A demo of the same you can see in the video below where the attack is carried out by Apple Lightening Cable while the cable charges the iPhone too.
Implanted Apple Lightning USB cable. I kind of want to make this my business card. 😈
(I just realized I never posted this variant, it’s been buried in the Hak5 video from earlier this year.) https://t.co/hS8RGw8CUG pic.twitter.com/QPqHHI0uen
— _MG_ (@_MG_) October 24, 2018
I had to explain about the Mr. Self Destruct USB and Bad USB Cables before coming to the main attraction of this post …
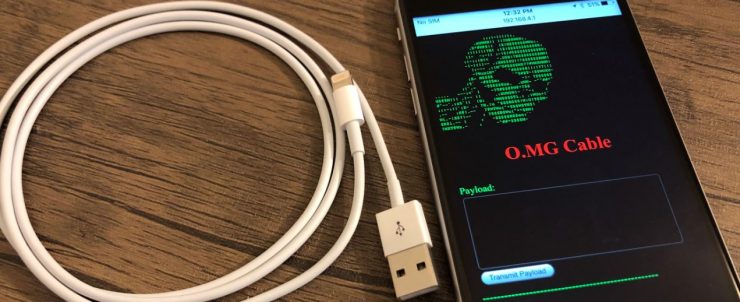
Hidden WiFi in USB Cables
The above two examples would have moved you in your chairs but now imagine you plug-in a USB cable and it spawns a back connection and someone start controlling your machine remotely, while the USB Cable we talking about would be as real as any Apple cable can get. See this video to get the idea of what I am saying
You like wifi in your malicious USB cables?
The O•MG cable
(Offensive MG kit)https://t.co/Pkv9pQrmHtThis was a fun way to pick up a bunch of new skills.
Not possible without help from: @d3d0c3d, @cnlohr, @IanColdwater, @hook_s3c, @exploit_agency #OMGCable pic.twitter.com/isQfMKHYQR
— _MG_ (@_MG_) February 10, 2019
You can follow the project page at O.MG Cable , although at the time of writing the developer hasn’t shared the project details and left it with a note saying
I spent about 5 solid weeks chasing this project as a way to also pick up a bunch of new skills. I will be publishing information related to much of that. (using the mill to get this level of detail, etc)
I am sure , the same will be updated in coming days for our consumption.
MG also plans to get these handed out to people who may be requiring these , again he has not worked out the details of mass manufacturing but I am sure if he can get in touch with Scotty Allen , The China iPhone guy could help him out – although they both are from a very separate industry. Let see how the project is revealed nonetheless it is another extra ordinary built-up which would have dynamic utilization by all sorts of tech folks.
Conclusion
Stop using cables and USB devices which aren’t yours, Buy one or be prepared for what you have read and seen above. IT Administrators would need to enforce better policies to ensure such malicious devices do not end up on their networks while also educating their users on what to expect. Make sure to use a VPN, Something which is good for viewing Netflix or to ensure your online privacy.
While it is worthy to mention the work done by MG is brilliant and you all should follow him @_MG_ so you may keep in touch with his future projects.
What do you think about the Project ? and Will you make a change in your USB-Cable Policies after knowing it is this cable to compromise your devices. Do you think such projects and concepts would be used for malicious purposes ?











[…] . Supply hyperlink […]
[…] cable, what could it possibly do aside from charge your phone?” What if someone embedded a WiFi module within the cable? That has been done and it’s a sneaky way to gain access to a user’s […]