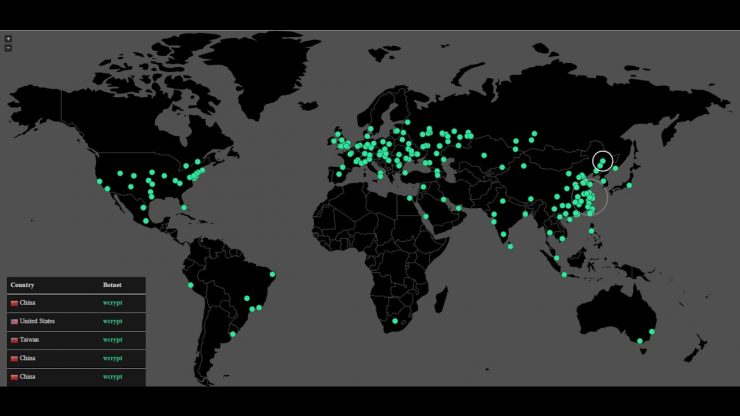
On Friday, huge wave of cyber-attacks hit tens of thousands of targets in at least 150 countries, the number of victims continues to grow as the latest count is more than 200,000. It is believed to be the biggest online extortion hitting hospitals, railroads, police, transportation and other organizations. Well that escalated quickly!
Dubbed as WannaCry, also referred as Wcry, WannaCry Decryptor is fast-spreading ransomware based on leaked NSA hacking tools. It is being used in combination with worm that causes it to spread automatically from one infected computer to the entire network. The ransomware first emerged in Britain and Spain,have spread across the globe, affecting mainly Russia (the hardest), US, Ukrain, Taiwan, Germany, France and even India.
Worldwide Impact
WannaCry attacks continued to spread across the world, affecting major institutions like U.K.’s National Health Service, Russia’s Ministry of Interior, Chinese government agencies, Germany’s Deutsche Bahn rail system, automakers Nissan Motor Co. and Renault SA, PetroChina, logistics giant FedEx Corp and company and hospital computer systems in Eastern Europe, the U.S. and Asia.
How It Works
Apparently victims are tricked into opening malicious phishing emails that appear to contain invoices, job offers, security warnings, and other legitimate files. Since the file is encrypted, most of the security systems do not identify the ransomware before it is downloaded. But typically Ransomware does not spread this quickly with phishing techniques, then what is new with this variant of WannaCry and what exactly would have created this much havoc.
Here comes the holy crap “EternalBlue”-a software exploit that was developed by NSA and made public by a group called ShadowBrokers in April. ETERNALBLUE takes advantage of security flaw in Microsoft’s Server Message Block (SMB) protocol to spread rapidly. Seemingly it is a worm-like process in which the infected computer scans other computers in the network to create damage. Once a computer is infected with malware it will spread to any connected Windows PC that has not been updated to guard against ETERNALBLUE. Program encrypts most of the user files including office, image, movie, database and email files, and demands a ransom of at least $300(in Bitcoin) through a message posted on computer’s screen.
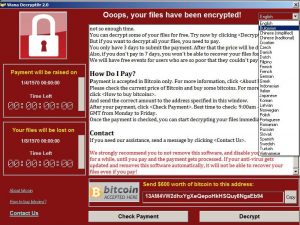

Ransomware was Halted Temporarily but not Over yet!
The attack was quickly responded as the initial WannaCry outbreak was slowed on Friday, though accidentally. A 22-year-old information-security professional at MalwareTech noticed a web address in the code, when analyzed he found that the address was not even registered. The moment he set up a server at that address, it turned out to be the kill switch as the WannaCry sample his team was analyzing, stopped infecting machines.
But still it’s not over yet as other variants with no kill switch are discovered and by Monday fewer aftershocks have been reported.
Microsoft Response and Blame Game
Microsoft immediately announced security patches for older versions for free. Before the attack, Microsoft had made the fixes for older versions available to those who paid extra for technical support.For current versions security update was released in March. With the 1.243.297.0 update, Windows Defender Antivirus detects the malware as Ransom:Win32/WannaCrypt, in Windows 10.
Microsoft president and chief legal officer Brad Smith said in his blog post:
“We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world. Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage”
He criticized NSA losing control on software stockpiling, saying
“An equivalent scenario with conventional weapons would be the U.S. military having some of its Tomahawk missiles stolen.”
How to Protect Yourself
- Install and maintain anti-malware software, firewalls and email filters.
- Update your windows machine and install security update MS17-010.
- Disable Message Block Service on computers within the network.

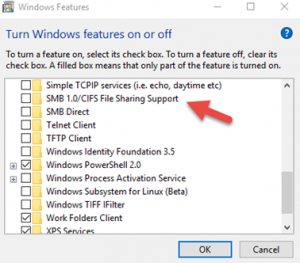
- Be careful when clicking links.
- Be cautious when opening email attachments particularly Zipped files.
- Microsoft recommends Device guard for Business and Office 365 Advanced Threat Protection for blocking emails with malware.
- British National Crime Agency tweeted an info graphic of “Do’s and Don’ts” to help protecting from ransomware.
This Ransomware attack on such a massive level is indeed a wake-up call for companies,governments and customers, as the cybercriminals have become more sophisticated and organized than ever before.More action is needed to minimize the attacks and make online lives safer.
Update : Decrypt your Files using WannaKiwi and WannaKey
Do Not Reboot your Machine if you are infected with WannaCry that is the only hope for an infected machine.















Add comment