In an era of escalating cyber threats, enhancing network security is paramount.
This article explores a comprehensive approach to network protection, encompassing network scanning, vulnerability and patch management, user access controls, network segmentation, and employee training.
Highlighting best practices and their importance, it provides critical insights for organizations aiming to bolster their defenses and safeguard their data effectively.
Dive in to understand the intricacies of implementing robust security measures in today’s digital landscape.
Key Takeaways
- Regular network scans and vulnerability management are crucial for identifying and addressing vulnerabilities.
- Patch management policies should be established to ensure timely updates and prioritize critical patches.
- User access controls, such as strong authentication mechanisms and regular access reviews, help prevent unauthorized access.
- Network segmentation limits the spread of attacks and allows for different security controls based on data sensitivity.
Network Scanning Techniques
Continually, organizations should employ a variety of network scanning techniques to identify potential vulnerabilities and strengthen their overall security posture. Utilizing robust network scanning tools, IT teams can probe their networks for open ports, weak configurations, and other potential weak points. These tools automate the often tedious task of scanning, enabling faster and more accurate detection.
However, identifying vulnerabilities is just the first step. Equally important is vulnerability prioritization, which involves analysing scan results to identify the most critical issues that need immediate attention. This process helps ensure that resources are allocated effectively, addressing high-risk vulnerabilities first.
This combined approach of network scanning and vulnerability prioritization is a fundamental component of a robust cybersecurity strategy.
Here are some of the most popular network scanning tools for :
- Burp Suite: Best for comprehensive web vulnerability scanning
- Detectify: Best for ease of use and automation
- Intruder: Best for cloud-based network security
- ManageEngine OpManager: Best for real-time network monitoring
- Tenable Nessus: Best for vulnerability analysis
- Pentest Tools: Best for penetration testing
- Qualys VMDR: Best for cloud security compliance
- SolarWinds ipMonitor: Best for large-scale enterprise networks
Effective Vulnerability Management
A comprehensive vulnerability management process is an essential aspect of network security, encompassing the identification, analysis, prioritization, and remediation of potential network vulnerabilities.
Utilizing advanced vulnerability scanning tools, organizations can automate the identification of security loopholes in their network infrastructure. The process doesn’t end at identification; the data gleaned from these scans require careful analysis.
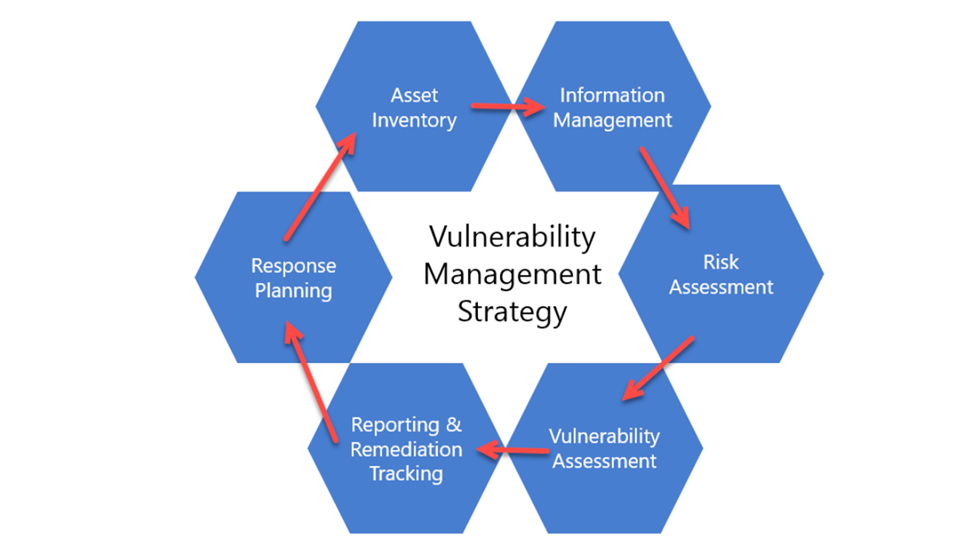

Vulnerability prioritization becomes a critical step here, enabling teams to focus their efforts on the most critical threats first, ensuring optimal use of resources. Once prioritized, vulnerabilities must be remediated promptly, necessitating a robust patch management program.
The continuous cycle of identification, analysis, prioritization, and remediation forms the backbone of an effective vulnerability management strategy, providing a proactive approach towards enhancing network security.
Implementing Patch Management
Building on the concept of vulnerability management, an equally significant aspect of network security is the implementation of a robust patch management policy. This involves identifying, acquiring, installing, and verifying patches for systems and applications.
- Patch deployment strategies: An effective strategy ensures that patches are deployed promptly and efficiently. It may involve automated systems for large networks, or manual patching for smaller, more sensitive systems.
- Patch testing methodologies: Before deploying a patch, it should be thoroughly tested in a controlled environment to check for compatibility issues or other potential problems.
- Continuous monitoring: Post-deployment, it’s crucial to ensure patches are working effectively and haven’t introduced new vulnerabilities.
With these steps, organizations can fortify their defenses, keeping their network secure and resilient to potential attacks.
User Access Control Measures
Implementing robust user access control measures is a crucial step in bolstering network security and minimizing potential threats. The bedrock of these controls is enforcing password complexity requirements, ensuring that all users have unique, hard-to-crack passwords.
This involves mandating a mix of uppercase and lowercase letters, numbers, and special characters. While ensuring the set conditions are not so stringent that users start making sequential passwords which are even easier to brute-force.
Coupled with this, periodic password changes can further deter unauthorized access. Yet, password measures alone may not suffice. Hence, implementing multi-factor authentication (MFA) is advised. MFA enhances security by requiring users to provide two or more verification factors to gain access.
This could be a combination of something they know (password), something they have (security token), or something they are (biometric verification).
These stringent measures, when applied correctly, greatly enhance network security. User awareness about limiting their cyber foot print is critical aswell.
Importance of Network Segmentation
In the organization’s pursuit for enhanced security, network segmentation emerges as a vital component. It essentially divides a network into several smaller parts, each acting as a separate entity. This approach yields significant benefits, especially in terms of bolstering the overall security posture.
- Containment of threats: Segmentation restricts the lateral movement of threats, thereby limiting the spread of attacks.
- Improved performance: By reducing network traffic, segmentation enhances the operational efficiency.
- Tailored security policies: Different segments can have unique security policies based on their specific requirements.
Implementation of network segmentation, however, necessitates careful planning, along with regular monitoring and updates, to ensure its effectiveness in providing a robust defence against evolving cyber threats.
Firewalls and Access Control Lists
With the implementation of network segmentation, the utilization of firewalls and access control lists becomes an integral part of securing an organization’s network infrastructure.
Firewalls, when correctly configured, serve as a robust line of defense against unauthorized external access. They scrutinize inbound and outbound traffic based on predefined rules, blocking those which don’t comply.
Access control lists, on the other hand, enforce access control policies, defining who or what is allowed or denied access to a network resource. Both these tools, when used in conjunction, provide a formidable barrier against cyber threats.
However, their effectiveness is largely contingent on the accuracy of their configuration and the appropriateness of the applied access control policies. Regular reviews and updates are essential to maintain a robust defense.
Here are some of the most popular enterprise-scale firewalls:
- Cisco ASA
- Fortinet FortiGate
- Palo Alto Networks Next-Generation
- Cisco Meraki MX
- Zscaler Internet Access
Employee Awareness Programs
Beyond the technical measures such as firewalls and access control lists, a crucial component in enhancing network security lies in the establishment of robust employee awareness programs. These programs aim to equip employees with the knowledge and skills necessary to detect, prevent, and respond to potential security threats. They play a pivotal role in phishing prevention and incident reporting, as employees are often the first line of defense against such attacks.
Regular training sessions on phishing prevention and safe online practices.
Hands-on workshops for recognizing and reporting suspicious activities.
Simulation exercises to test employees’ understanding and response to potential threats.
Cybersecurity Training Best Practices
A considerable part of an organization’s defense strategy should be dedicated to the implementation of effective cybersecurity training practices.
The cybersecurity training benefits are manifold and directly contribute to enhancing an organization’s overall security posture.
Training modules should be designed to address the most pertinent threats, including but not limited to, phishing, ransomware, and social engineering attacks.
To make the training more effective and practical, organizations can conduct phishing simulation exercises. These exercises allow employees to experience first-hand how these attacks occur, which in turn enhances their ability to identify and respond to real-life situations.
Additionally, regular updates to the training curriculum are necessary to keep pace with evolving cyber threats.
Plenty of online platforms, like Lumify Learn and Skillshare, provide online cybersecurity training, so it shouldn’t be hard to find one that addresses your company’s needs. Ultimately, a well-trained workforce is a fundamental layer of any robust cybersecurity strategy.
Conclusion
In conclusion, robust network security necessitates a multifaceted approach incorporating:
- Regular network scanning
- Efficient vulnerability and patch management
- Rigorous user access controls
- Strategic network segmentation
- Consistent cybersecurity awareness training
These practices, when meticulously implemented, offer a formidable defense against cyber threats, thereby securing an organization’s data and systems.
Thus, enhancing network security is a paramount concern, requiring ongoing commitment and strategic planning to ensure effective protection.











Add comment