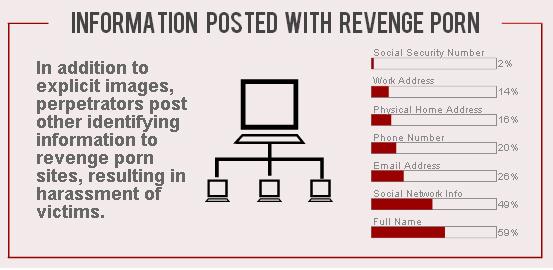
You read it right, If you’ve had a nude photo ever taken, you might be nervous about where it could end up. Your phone may be hacked or a relationship gone wrong, meaning the “Revenge Porn” picture could be made public without your say so, such act is also known as Image Based Abuse.
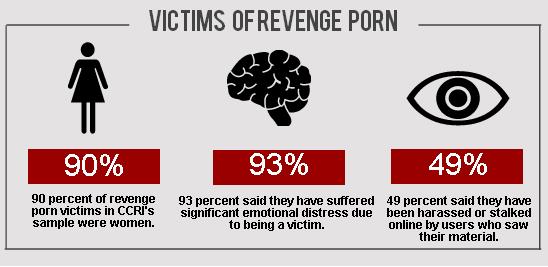

Now, Facebook is partnering with a small Australian Government agency to prevent sexual or intimate images being shared without the subject’s consent. Interesting part is how Facebook plans to make it work, although technically it is a very interesting Idea its just like taking “ownership” of your images before they get viral by some nasty users.
Key points of Facebook Image Based Abuse Prevention / Revenge Porn
- Facebook working with e-Safety Commissioner to block image sharing using innovative idea
- You flag your photos if you don’t want them circulated, then they cannot be uploaded again
- Images sent to database won’t be stored (Well)
e-Safety Commissioner Julie Inman Grant said victims of “image-based abuse” would be able to take action before photos were posted to Facebook, Instagram or Messenger.
We see many scenarios where maybe photos or videos were taken consensually at one point, but there was not any sort of consent to send the images or videos more broadly
How will Facebook Image Based Abuse Prevention Work ?
Image based prevention or Revenge Porn is pilot project which might or might never roll out for all users of Facebook or it might after meeting some success with the Australian governments. How Facebook Revenge Porn Protection Works
- If you fear image image based abuse or revenge porn, you just send the same images you fear might get on the internet to yourself on the messenger, yup that’s right, might seem weird .
- Once the image is sent via Messenger, Facebook would use technology to “hash” it, which means creating a digital fingerprint or link.
- They’re not storing the image, they’re storing the link and using artificial intelligence and other photo-matching technologies to create a digital identification for the same image.
- If somebody tries to upload that same image, which would have the same digital footprint or hash value, it will be prevented from being uploaded.
- If the program goes according to plan, the photo will never show up on Facebook, even if a hacker or your ex tries to upload it.

WEIRD – Facebook Image Based Abuse
The concept is great which might seem weird but this also implies that if you want to create a digital fingerprint or link of your “compromising images” you will need to upload the image before some hacker or your ex tries to upload, so is Facebook implying that users start uploading their nudes just to be on safe side ?
The other possibility here is that users should keep their *such* images saved so in case of a phone hack or breakup and if they fear such images going on the wild, they open up their “respect box” and quickly start sending all those images … Again weird ? but as they say “desperate times call for desperate measures“


Facebook Image Recognition in the Long Run
Facebook’s head of global safety, Antigone Davis, said Australia was one of four countries taking part in the “industry-first” pilot which uses “cutting-edge technology” to prevent the re-sharing on images on its platforms.
Image Recognition of Facebook has evolved alot and their above mentioned feature will also add to the same, the same digital print will also be used to perform other stuff
- Detect when a certain image was uploaded on Facebook
- Who was the first uploader of an image
- How many Pages shared the same image
Interesting World we Live in, whats your take on this ?










Add comment