A car theft was caught on a security cam, which was no ordinary theft as car-jackers used Relay Attack on a Tesla vehicle to unlock the car and drive it away, the complete attack is clearly visible although thief had a hard time unlocking the charging cable. Let see the theft and what is Passive Entry along with Relay Attack.
Watch the Entire theft of Tesla S Model using Relay Attack
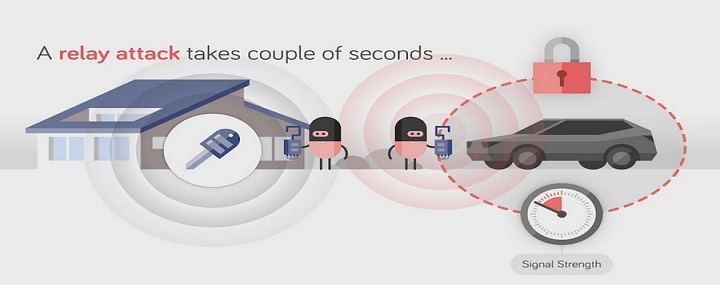
When the thieves approach the vehicle we can see one of the thieves searching around for a signal to boost with a device (relay box). Once he finds the key fob signal, he stays there and send the signal to his partner who is standing next to the vehicle.
Once the car is unlocked, they both hilariously struggle to unplug the vehicle from the charging cable,even though they successfully unlocked the car. Once unlocked, One needs to simply click on the button of the cable’s handle and pull the plug. It might be possible that it is their first Tesla theft ? because its funny how they are sophisticated enough to know how to do a Passive Entry Relay attack on a Tesla vehicle, but they don’t know how to unplug it.
What is a Passive Entry Relay Attack
To understand the Relay Attack, let me explain to you what Passive Entry system is in Tesla Vehicles.
Passive Entry System : A passive entry system is a convenience feature that allows anyone with an associated programmable key (commonly known as key fob ) or key card to enter the vehicle and start it. As long as the key fob is in close proximity to the vehicle, usually within a few feet, you can leave it in your pocket, purse, or bag, enter the car and push a button inside the vehicle to start the engine and drive. Even with remote drive capability the key fob has to be the in the car before the care can actually be driven away.
Relay Attack : In a relay attack, a thief uses a device that captures the weak signal coming from the key fob. The device commonly known as a “relay box,” boosts the strength of the captured signal and relays it to another device which is close to the target vehicle, enabling the thief to enter the vehicle.If all the thief wants to do is steal the contents of the vehicle, that could be the end of it. If the thief wants to take the car, they need an additional method of starting it, such as reprogramming the car via the vehicle diagnostic port or using the captured signal with another device to create a duplicate key fob. In Case of Tesla, once you get the key fob and you unlock the Tesla you do not need to duplicate the fob and can go in “Drive” without that.
How to Prevent Relay attack on Tesla Vehicles
The company shared ‘tips’ to help prevent such Relay Attacks on their cars, which include Disabling Passive Entry (Controls > Settings > Doors & Locks > Passive Entry > OFF). But if you want to have the convenience of passive entry, you can also key your key fob in some signal blocking pouch (made on Faraday cage concept) , that would block the signal and also prevent attackers from executing Relay Attacks.
Keeping in view such attacks, Tesla recently released a new optional ‘PIN to Drive’ feature that requires to enter a PIN in the vehicle before putting it in ‘drive’ ensuring that even if hackers are successful in their relay attack the vehicle can not be driven off with. But if you want to keep all the features on you can always use the Faraday Cage Pouch












Add comment