Stealing PINs via Mobile Sensors
Most Smartphones, Tablets and other wearables are now packed with wide range of sensors such as GPS, accelerometer, magnetometer, proximity, gyroscope, pedometer, and NFC, to name a few. While these sensors can provide more features and functionalities to the end users, they also raise serious threats to the privacy and security of the users.


According to the new study published in International Journal of the Information Security, researchers at Newcastle University discovered such an attack that could allow hackers to potentially crack your PIN and other information by monitoring sensor’s data, like the angle and motion of your phone while you are typing or navigating through it.
How it works
The team wrote a malicious Javascript file called PINLogger.js that exploits the vulnerabilities in web browsers,uses standard APIs provided by W3C and has the ability to recognize tilt patterns associated with “Touch Signatures” that a user uses regularly.


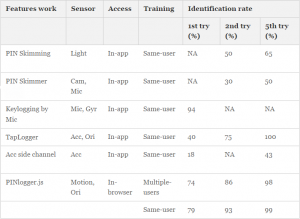
In the likely scenario, the user visits a website controlled by an attacker, the JavaScript code embedded in webpages, starts listening to the sequences of motion and orientation sensor .By analyzing these sequences, it infers the user’s PIN using an artificial neural network. Based on a sample set of fifty 4-digit PINs, PINlogger.js is able to correctly identify PINs in the first attempt with a success rate of 74% which increases to 86 and 94% in the second and third attempts, respectively. While a random attack may guess the PIN with 2% accuracy on first attempt, hence by comparison PINLogger.js achieves dramatically a higher success rate than a random attacker.
Furthermore unlike in-app attacks this in-browser javascript based attack does not require any app installation and user permissions.
Susceptible Browsers
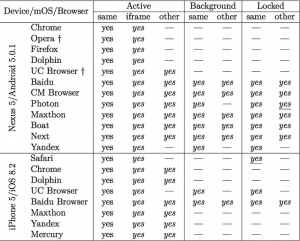
The extent of vulnerability to various attacks varies browser to browser and to a lesser degree also depends on which operating system the browser runs on.
Browser provided by Chinese-US Web services company Baidu has the most chances of passing sensitive data from malicious websites open directly or in background tabs, even when the device screen is off. However Safari, Firefox and Google Browser for iOS restricted access to sensor data when the sites were loaded in background tabs.
Fix PinLogger.js Hack
Results were sent to the makers of these browsers. Mozilla and safari partially fixed the problem by suspending the availability of sensor data when pages are hidden but this also restricts the useful applications to run.
Although this in-browser attack via mobile sensor is new but the in-app vulnerabilities have been reported and exploited for years. Yet the problem is not fixed and this will probably expand with the rapid development in sensor-enabled devices in the IoT.
The Study concluded that designing a practical solution seems to be very complex hence a general mechanism for secure and usable sensor data management remains a crucial open problem for future research. To achieve a balance between Security and Usability, an extensive study is required towards designing a “permission framework”.
Another good read is the User Data made available by Maryam Mehrnezhad on reading sensor data upon entering 4 Digit PIN














[…] https://blog.drhack.net/motion-detection-pin-logger-hack/ […]