“Hey Siri” is supposed to be returned with a helpful voice of Apple assistant which is always available to help you, but Hackers might abuse the new Siri Shortcuts feature.
Apple introduced Siri Shortcuts with iOS 12, enabling users and developers to make better use of Siri and automate a number of tasks. IBM’s security division has stumbled upon a possible Siri Shortcut Vulnerability where it could be used for malicious purposes, including tricking an iPhone users into paying ransom to avoid having their information released on the public.
What is Apple’s Siri Shortcut
Siri Shortcuts were introduced in iOS 12 that allows an app to expose its functionality to Siri. This enables Siri to suggest shortcut at relevant times based on various context. Shortcuts can also be added to Siri to run with a voice phrase on iOS, HomePod and watchOS.
Siri Shortcut feature can be enabled via third-party developers in their apps, or custom built by users downloading the shortcuts app from the app store. Once downloaded and installed, the Shortcuts app grants the power of scripting to perform complex tasks on users’ personal devices.
If you can see the explanation of Siri Shortcut in this video for better understanding if you desire
Siri Shortcut Exploitation Threats
Using Siri for malicious intent, Shortcuts could be created for scareware, a pseudo ransom campaign to try to scare victims into paying a criminal by making them believe their data is in the hands of a remote attacker.
Using native shortcut functionality, a script could be created to speak the ransom demands to the device’s owner by using Siri’s voice. To lend more credibility to the scheme, attackers can automate data collection from the device and have it send back the user’s current physical address, IP address, contents of the clipboard, stored pictures/videos, contact information and more. This data can be displayed to the user to convince them that an attacker can make use of it unless they pay a ransom.
To move the user to the ransom payment stage, the shortcut could automatically access the Internet, browsing to a URL that contains payment information via cryptocurrency wallets, and demand that the user pay-up or see their data deleted, or exposed on the Internet. All that can be done with native UI , where the user would really think that the Hacker has already taken over the device thanks to Apple own code.
The malicious shortcut can also be configured to spread to other devices by messaging everyone on the victim’s contact list, prompting them to download and install the same shortcut. This would be a cost effective and hard to detect distribution method, coming from a trusted contact.
How Does Siri Shortcut Hack Work ?
IBM’s X-Force security division discovered that it is possible to use a Siri Shortcut feature for malicious purposes, one such example is where a malicious shortcut is able to read information from an iOS device and then demand a fee from the user, all with the native Siri voice. Shortcuts issue is not an explicit vulnerability in Apple’s technology rather it is a feature which could be exploited by Hackers making use of their Social Engineering skills. IBM Research team further added
IBM X-Force conducted all of the research using native functionality of the Shortcuts app, so no exploitation of vulnerabilities was needed
Siri Shortcuts gives native capability to potentially send messages to contacts if the appropriate permissions are enabled
Siri Shortcuts is a native feature of iOS12; however, in order to utilize custom shortcuts, one has to download the Shortcuts app from Apple’s app store. If a user has installed “Shortcuts App” , malicious developers can either push their malicious shortcut or a legit app could get compromised and hackers might push their version of shortcut for a very old and trustworthy app.
[POC] Siri Shortcut Exploit Demo Video
The above video had showed an obvious shortcut named ‘Random’ , it could be named anything or it could be set to perform the action at anytime of the time or after triggering any certain activity. The shortcut shown above was configured to do following :
- Collect photos from the camera roll.
- Grab the contents of the clipboard.
- Get the physical address of the device’s location.
- Find the external IP address.
- Get the device’s model.
- Get the device’s current mobile carrier
Once above data is obtained the same shortcut is capable of doing the following :
- Siri Shortcut can message the information to an external party; this data can also be sent over SSH to the attacker’s server using native functionality.
- Shortcut can set the brightness and volume of the device to 100%.
- Shortcut can turn the device’s flashlight on and off while vibrating at the same time to get the user’s attention and make them believe their device has been taken over and someone is doing these things remotely.
- Shortcut can be made to speak a ransom note as you have seen in above video which can include convincing personal details. For example, it can indicate the IP address and physical address of the person and demand payment, this will make the user believe that the hacker has indeed obtained access of the device.
- Shortcut can be further programmed to display the spoken note in a written alert format on the device.
- To nudge the user to pay up, the Shortcut can be configured to open a webpage, accessing a URL that contains payment information to a cryptocurrency wallet, or a phishing page demanding payment card/account information.
- To spread around, and since Siri Shortcuts can be shared among users, the malicious Shortcut could also send a link to everyone in the user’s contact list giving it a “worm like” capability, such a feature would be very easy to deploy.
Siri Shortcut and Personally Identifiable Information
Siri Shortcuts does allow access to some system files on the phone. However, it does not allow access files with PII [personally identifiable information] but Siri Shortcuts does have native functionality to give the victim’s physical address, IP address, photos, videos and more which I would say is enough to “personally identify a user“
How Serious Siri Shortcut Vulnerability Is
Protect Your Siri Shortcuts
Every second article on this blog has a line or two about protecting our privacy and passwords, it would be unfair If i do not share the same for this article issue.
- Never install a Shortcut from an unauthorized source
- Check the permissions that the shortcut is requesting and never give permission to portions of your phone you are not comfortable with. Things like photos, location and camera could be used to obtain sensitive information. A gallery shortcut app might require permission to the photos but a music app requesting permission of your camera roll should put you on alert.
- Use the show actions button before installing a third-party shortcut to see the underlying actions the shortcut might take. Look for things like messaging data to numbers you don’t recognize, emailing data out, or making SSH server connections to servers

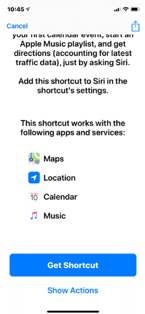
After installing the shortcut see what permissions and actions it can perform - Validate anything you install on your mobile device as Shortcuts allows you to see everything the script is capable of before installing
- Be mindful when running a Siri Shortcut and only enable actions that are needed
As technology advances we see features which make things easy for us but along with the same ease come threats which evolve along with the counter measures. What do you think about this threat which comes along Siri Shortcut ?











Add comment