You might be of opinion that your password is complex and safe, but what if I tell you that your Password has been breached already? You should know if your Password was ever revealed in any prior data breaches so you may stop using them.
I have already shared about a service which allows you to see if your Email Address surfaced in any Hacks on the internet, a good way to know if you need to take some actions and secure your internet accounts.
But that is not enough of checking , what if someone else got their account hacked and their password was exposed , how will you know that ?
Why someone will use my Password ?
We have people with same name,hobbies,habits and date of births. Is it not possible that there are 2 girls named Mary both having Capricorn… how impossible it is that they decide to keep Mary@Capric0rn as their password ? it’s not.
One Gone All Gone
If account of any one of Mary gets breached her password (we all know encrypted passwords get cracked eventually) is shared it means the other Mary got her account breached aswell…
Is your Password still Safe and Valid for Use ?
Have I been pwned? allows you to check your password if it has been breached.
On HIBP Passwords page , there’s a search box where you can enter a password and it will tell you if it exists on the service. For example, if you test the password “StrongPassword“:
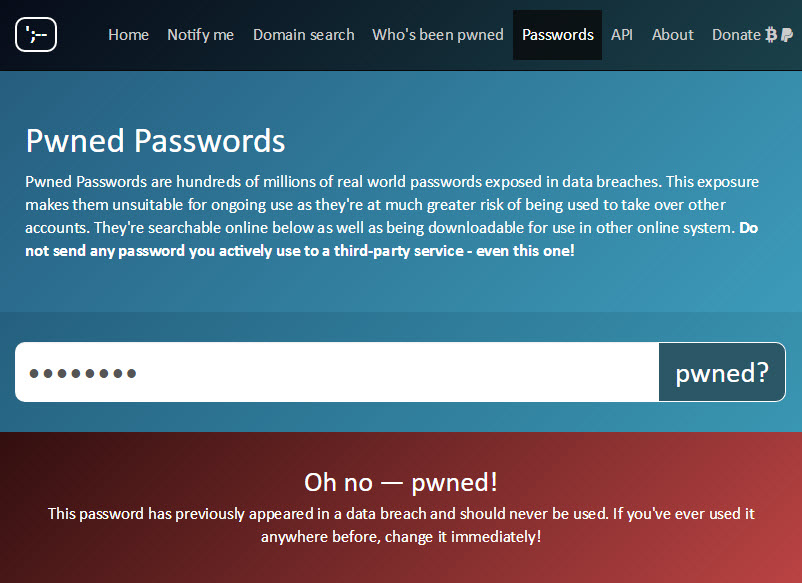

The point of the web-based service is so that people who have been guilty of using sloppy passwords have a means of independent verification that it’s not one they should be using any more. Mind you, someone could actually have an exceptionally good password but if the website stored it in plain text then leaked it, that password has still been “burned”.
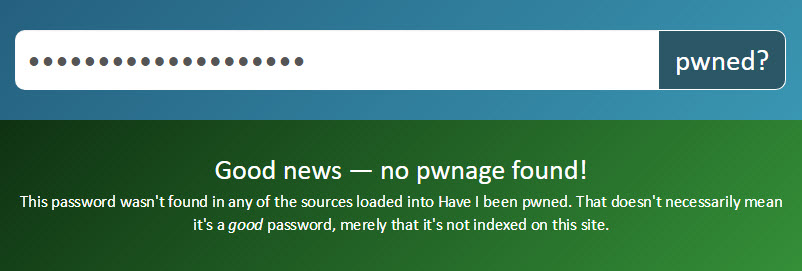
If a password is not found in the Pwned Passwords set, it’ll result in a response like this:
tech-savvy people using this service to demonstrate a point to friends, relatives and co-workers: “you see, this password has been breached before, don’t use it!” If this one thing I’ve learned over the years of running this service, it’s that nothing hits home like seeing your own data pwned.
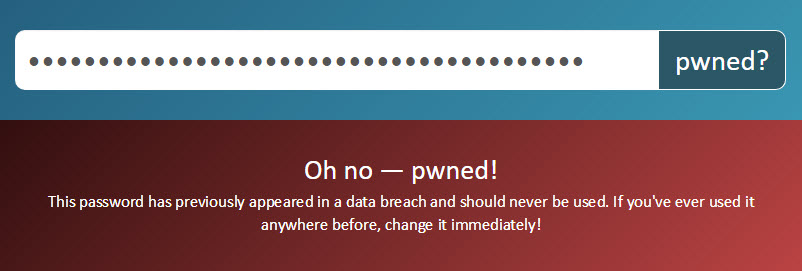
You can also search for a SHA1 hash of the password. Taking the password “p@55w0rd” as example, a search for “ce0b2b771f7d468c0141918daea704e0e5ad45db” (the hash itself is not case-sensitive so “CE0B…” is fine too) yields the same result:
The service auto-detects SHA1 hashes in the web UI so if your actual password was a SHA1 hash, that’s not going to work for you. This is where you need the API which is per the existing APIs on the service, is fully documented. Using this you can perform a search as follows:
And as for that “but the actual password I want to search for is a SHA1 hash” scenario, you can always call the API as follows:
GET https://haveibeenpwned.com/api/v2/pwnedpassword/ce0b2b771f7d468c0141918daea704e0e5ad45db?originalPasswordIsAHash=true
That will actually return a 404 as nobody used the hash of “p@55w0rd” as their actual password (at least if they did, it hasn’t appeared in plain text or was readily crackable). There’s no response body when hitting the API, just 404 when the password isn’t found and 200 when it is, for example when just searching for “p@55w0rd” via its hash:
GET https://haveibeenpwned.com/api/v2/pwnedpassword/ce0b2b771f7d468c0141918daea704e0e5ad45db
Be Safe !! Change your Passwords frequently 🙂













[…] if you follow my guide on keeping secure and strong passwords these types of data breaches are beyond our control and leave us badly exposed with threat of our […]
[…] second article on this blog has a line or two about protecting our privacy and passwords, it would be unfair If i do not share the same for this article […]