- Year 2017 has already seen some destructive ransomware attacks like WannaCry and Notpetya, following these another attack is now on the rise.Dubbed Bad rabbit the new ransomware attack surfaced on Tuesday hitting major news and media outlets. However unlike its predecessors Bad rabbit is not that bad!
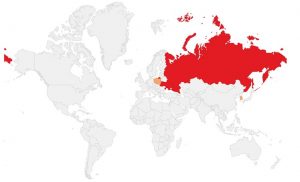
The ransomware initially targeted a number of big media outlets and news agencies in Russia and Ukraine, and also compromised few websites in Turkey, Germany, Bulgaria, Poland and South Korea.
Russian news agency Interfax, Odessa International Airport and payment system of Kieve metro are among the victims.
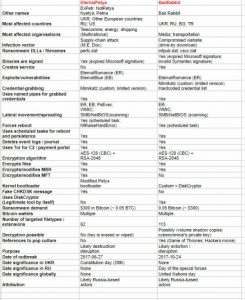
Bad Rabbit vs Notpetya
The ransomware apparently uses methods similar to those used in Notpetya for demanding ransom. It also shares a slice of basic code with Notpetya. Also the web servers for initial distribution of software are connected. The sites linked to Notpetya are being used to host distribution channels for Bad rabbit.
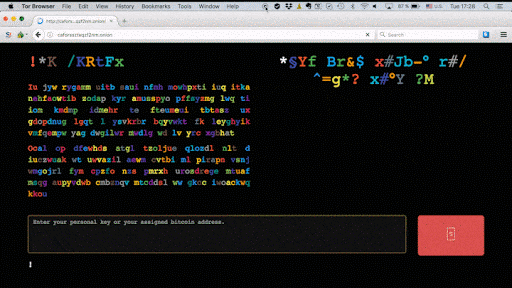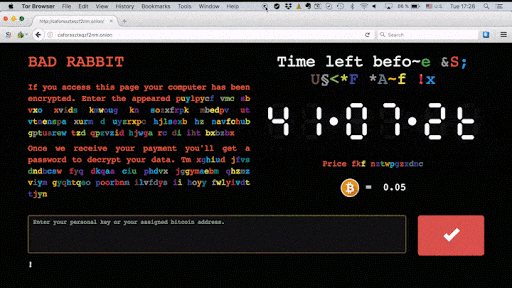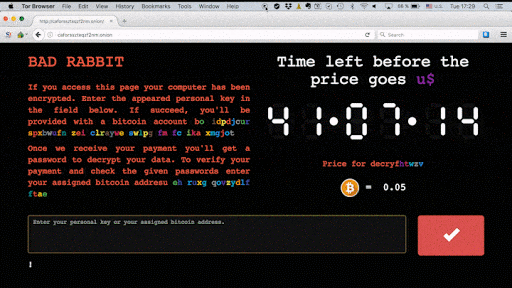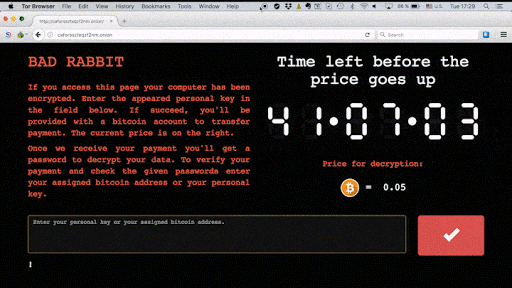
However there are some notable differences. Unlike Notpetya that spread through passive means, Bad Rabbit is a drive-by attack. It requires potential victims to download a fake Adobe Flashplayer installer from infected websites and then manually execute the .exe file, thus infecting themselves. Infected users are then directed to a Darknet site where they are asked to pay 0.05 bitcoin.
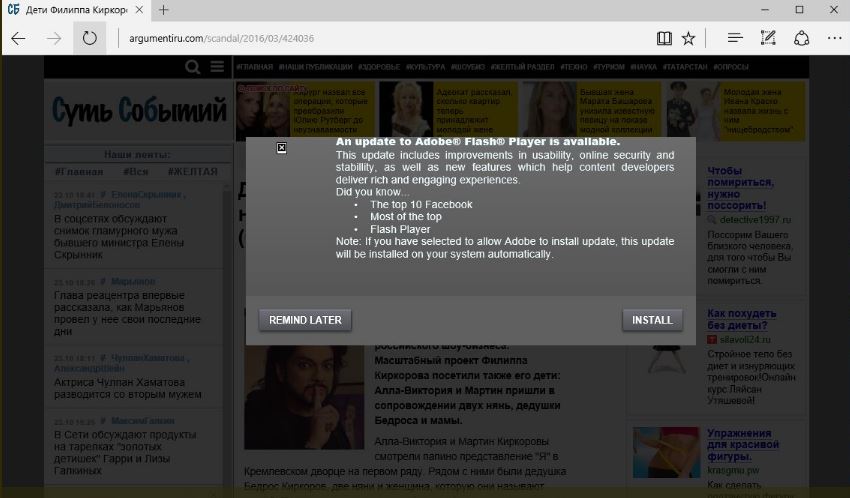

It might be surprising but Abode Flash Player fake download is still a thing .

A countdown with ransom note shows the time left to make payment before the ransom price increases.
How Bad Rabbit Spreads
Eternalblue in Wannacry and Notpetya exploited vulnerability in SMB for spreading quickly like a worm. Bad rabbit did used SMB but in a different way to propagate internally on the network. Furthermore exploits of WebDAV (the Web Distributed Authoring) and Versioning extensions to the Hypertext Transfer Protocol (HTTP) are also used in Bad rabbit that allows for a collaborative editing between users across a network. Researchers found that Mimikatz tool was also being used to extract credentials of machines on infected network.
Criminal behind Bad rabbit seems to be a movie fanatic. As the malware code makes references to the hit series of Game of Thrones including the two dragons. It also tries “four most common” passwords from 1995 movie Hackers – “Love, God, Secret,Sex” while trying to propagate.
How to keep Bad Rabbit at Bay
There is a technique which works sort of “vaccine file” that will prevent Bad Rabbit from infecting your machine. If you are running the system as an administrator and create a file named “cscc.dat” in “C:\Windows\“, the malware will not run. You can create this file by creating a txt file and renaming it to cscc.dat and save it in C:\Windows\.
If your PC is already infected with BadRabbit, I would not recommend that you pay the ransom – the moment people stop paying ransoms is the time these “ransomwares” will seize to exist.
To protect yourself against ransomware, like Bad Rabbit:
- Install a good antivirus on all devices possible, including on your smartphone. Antivirus software will block ransomware, should you encounter it.
- Updating all of your software whenever a new version becomes available can help prevent ransomware from exploiting a software vulnerability to infect your device. While in this case victims were prompted to update their Adobe Flash, and thought they were doing the right thing, it is important to only update programs from official distribution channels. (Be skeptic about Websites which tell you “install / upgrade XYZ” .
- Most important is being cautious, as it can greatly help avoid ransomware. Although this time legitimate websites were infected, in general, you should stay away from shady websites, be careful what you download and not open any links or attachments sent to you from a suspicious or unknown sender.
- Many people don’t think an ordinary Word or Excel document can lead to something malicious downloaded, which is why cybercriminals like using them for their attacks. Malicious attachments, sent in the form of a Word or Excel document, often request Macros to be enabled, which allows the document to download malware, including ransomware, from the internet.
- Backing up your data on a regular basis will help avoid data loss, in case you fall victim to ransomware. If you regularly back up your data, while offline, to an external hard drive that is not connected to the internet, you greatly lower the risk of anyone touching your data through the internet.
- Again – DO NOT PAY THE RANSOM
How to Clean your Bad Rabbit Infected Machine
If you have already fallen prey to Bad Rabbit , You can is do a system restore to an earlier stage or start your system in Safe Mode and do a full system scan with your antivirus, follow these steps to clean your Bad Rabbit Infected Machine
- Turn off your Machine
- Turn on your Machine and Start it in Safe Mode with Networking
- Log on to your Bad Rabbit Infected User
- Open your Browser and install a good Antivirus which catches Bad Rabbit (most do that)
- If you can not start in Safe Mode with Networking ,keep on reading
- Restart your machine into “Safe Mode with command prompt“
- once loaded type “cd restore“
- Type ” rstrui.exe”
- restore to an early backed up restore point – if you have one
Following the above steps should fix your Bad Rabbit infected system
How much Bad Rabbit Hackers have earned
Bad Rabbit listed 2 BTC wallet addresses where they were receiving payments
1GxXGMoz7HAVwRDZd7ezkKipY4DHLUqzmM
17GhezAiRhgB8DGArZXBkrZBFTGCC9SQ2Z
As of today total deposited BTC in their wallets is 0.0075359 which makes it 46.01 US Dollar. All the effort and harm they did for just $46 ? . Its good to see the decline in people paying ransoms to attacker as the trend of ransomware will die down when people will stop paying ransoms.












Add comment