If you’re using a popular Cryptocurrency App for Android, there’s a near guarantee that it’s vulnerable to at least one of the Open Web Application Security Project’s (OWASP) mobile top 10 vulnerabilities. Which means your Investment and Money is not safe and can be stolen by hackers

Valuable Crypto, Lucrative Target
Cryptocurrency might be a bubble (I disagree) but the bubble is valuable and at the time of writing Bitcoin is sitting at 15000 USD approx, when the stakes are so high it becomes a good target for the notorious hackers who would spend alot of time to get their hands on your Hard earned-mined-traded crypto.
The security audit was carried out on:
- 30 most popular cryptocurrency apps with more than 500,000 installs
- 30 with up to 500,000
- 30 with up to 100,000
Alarming results where obtained during the Security audit for Android Users :
- Apps with more than 500,000 downloads – 94% contained at least three medium-risk vulnerabilities, 94% lacked any back-end hardening or protection, and 94% were still using either the 21-year old SSL 3.0 or the 18-year old TLS 1.0 crypto protocols.
- Apps with 500,000 and less downloads – 84% contained at least two high-risk vulnerabilities, 61% were transmitting unencrypted data over HTTP, and 47% were vulnerable to man-in-the-middle attacks.
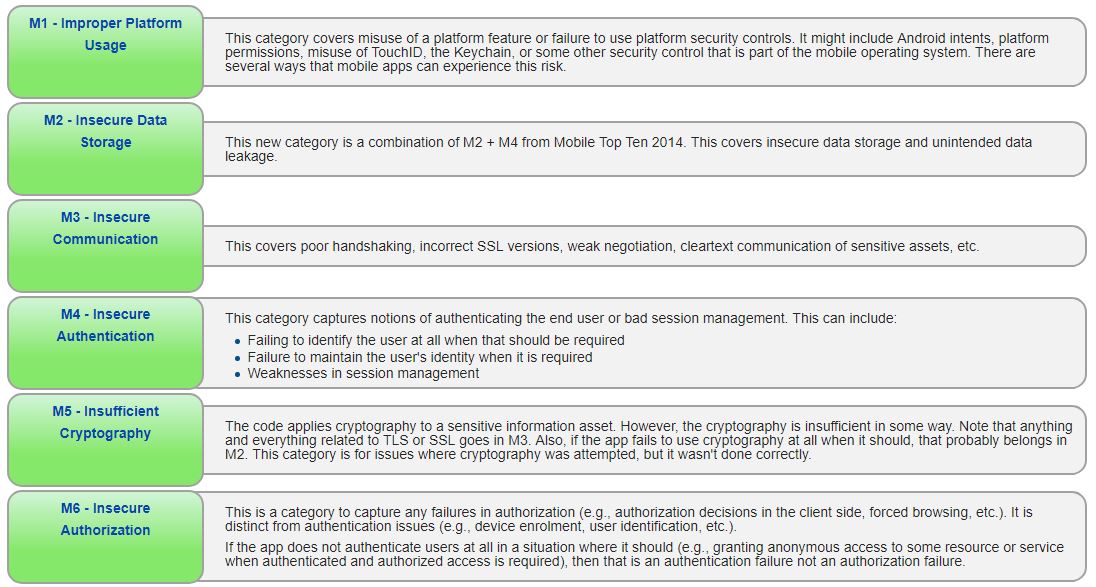
The most common OWASP vulnerabilities spotted during the Crytpocurrency App Test :
- Improper platform usage – Misuse of a platform features (like Android intents, TouchID, or keychains) or failure to use platform security controls
- Insecure data storage – Unintended data leakage
- Insufficient cryptography – Use of cryptography that wasn’t done correctly (including any SSL and TLS issues)


Risks involved with Cryptocurrency Mobile Apps
The risks are high, apps from the top 30 included alot of OWASP Vulnerabilities, as an example i’ll list the vulnerability and what security threat it poses.
- Unencrypted HTTP Protocol – The Crypto Mobile App uses HTTP protocol to send or receive data. The design of HTTP protocol does not provide any encryption of the transmitted data, which can be easily intercepted if an attacker is located in the same network or has access to data channel of the victim. [reference]
- Man in the Middle Attack – Improper or missing ‘hostname’ verification exposes mobile application users to MITM attacks under certain conditions. In simple words someone can hijack your account and take control of Crypto assets. [reference]
Test your Cryptocurrency Mobile App for Vulnerabilities
Follow the simple steps to test your mobile crypto app so you can see if the app is safe to use or not.[sociallocker]
- Download APK extension of your Crypto App through APK Mirror
Note: You may use any other APK downloading method / site - Open Mobile Application Security Website and click on “Choose File” to upload your APK file
- Wait for approximate 30 minutes for the detailed report to be presented to you
Note: The scan time depends upon complexity of uploaded APK and server load[/sociallocker]
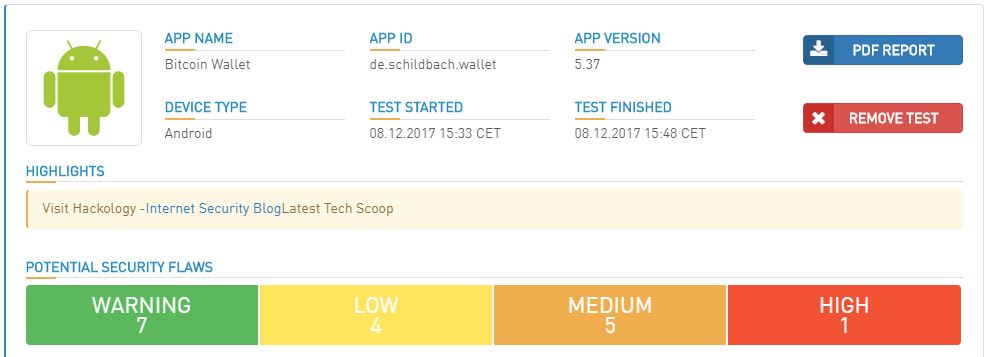
I conducted a Security Audit of “Bitcoin Wallet” App which came up with some serious vulnerabilities , which you can read on the next page. I showed which vulnerabilities were reported and listed how those can be exploited
Demo Security Report of a Cryptocurrency Mobile App
I opened Google Play and typed “bitcoin wallet” the first result was an app named “Bitcoin Wallet” with 500,000 installs.


I downloaded ‘Bitcoin Wallet’ app from APK Mirror ( Download from APK Mirror : bitcoin wallet). I opened the Security Audit Site and uploaded the APK File for auditing

After the file is uploaded the comprehensive report will be prepared, the preparation can take time depending upon the file size, complexity and server load, in my case it presented me with a 26 minute wait.

Once the Security report is ready it will automatically load and will give you a detailed analysis of your uploaded app.



The report gives out a summary on top and as you scroll down it will give you details of each vulnerability – False positives are always possible but why take risk ?
Some noticeable vulnerabilities discovered when I scanned “bitcoin wallet” which merit a mention :
- External Storage Access – A crypto wallet should not be allowed to write on external SD Card as external card can be accessed by any other Application even the notorious ones
- Weak Hashing Algorithms – Bitcoin wallet uses SHA-1 in file ‘com/suareup/okhttp/internal/Util.java’ encryption which is outdated and is prone to collusion attack.
- Missing Tapjacking Protection – Tapjacking can be used by an attacker to trick Bitcoin Wallet users into performing some sensitive actions in a legitimate application (e.g. send a payment) they do not otherwise intend doing.
- Use of HTTP – Bitcoin Wallet application is using HTTP URL at few locations which can be targeted by an attacker to perform MITM attack.
Conclusion
As you witnessed above I took a random Crypto Mobile wallet for test and it came up with few vulnerabilities which can cause the crypto users alot. You might never get targeted but why not to take precautions ?. If you are a cryptocurrency user the best practice would be to avoid using “Mobile Wallets” which keeps your private key on the mobile phone, All wallets should be offline preferably. You can always Ask Techie! for more guidance and help











Add comment