Hundreds of millions of Facebook users had their account passwords stored in plain text which were searchable by Facebook employees — in some cases going back to 2012. Facebook says an ongoing investigation has so far found no indication that employees have abused access to this data but it shows Facebook has either lied with us or they were not knowing what is going on with the “Code”. That also raises another point that their Code Audit is not up-to-the mark.
Employees Bypassed Facebook Security Protocol
The investigation so far indicates between 200 million and 600 million Facebook users may have had their account passwords stored in plain text and searchable by more than 20,000 Facebook employees. Facebook is still trying to determine how many passwords were exposed and for how long, but so far the inquiry has uncovered archives with plain text user passwords in them dating back to 2012. Passwords of Instagram are also included in this massive plain text password finding.
Facebook software engineer Scott Renfro said Facebook wasn’t ready to talk about details and numbers — such as the exact number of Facebook employees who could have accessed the data. Renfro said the company planned to alert affected Facebook users, The alert would include a change of password or not is yet not certain.
We’ve not found any cases so far in our investigations where someone was looking intentionally for passwords, nor have we found signs of misuse of this data. In this situation what we’ve found is these passwords were inadvertently logged but that no actual risk ’s come from this. We want to make sure we’re reserving those steps and only force a password change in cases where there have been signs of abuse.
Renfro said the issue first came to light in January 2019 when security engineers reviewing some new code noticed passwords were being inadvertently logged in plain text. Renfro said
We have a bunch of controls in place to try to mitigate these problems, and we’re in the process of investigating long-term infrastructure changes to prevent this going forward. We’re now reviewing any logs we have to see if there has been abuse or other access to that data
Facebook Protect the Graph – Not that Protected
Facebook published a statement in October 2014, where they stated how they secure passwords and how they go one step ahead and see for public breaches and match that data with “hashed” passwords on their own system to see if the breach has any data from Facebook. I will quote one sentence from the statement where they are outlining their proactive approach
This is a completely automated process that doesn’t require us to know or store your actual Facebook password in an unhashed form
Under the “Technical Details” of the same statement, serial 2 is worth quoting here
We hash each password using our internal password hashing algorithm and the unique salt for that person. Since Facebook stores passwords securely as hashes, we can’t simply compare a password directly to the database. We need to hash it first and compare the hashes.
Facebook states with confidence that all our passwords are encrypted and hashed. So how millions of passwords were being stored on internal servers for over a decade now ?
Although Facebook has never sent out a notification even when passwords surfaced on the web, so its better to check your passwords yourself and do not rely on Facebook.
Keeping Passwords (un)Secure
Facebook has made an announcement today (21 March 2019) where they have tried to break the news as politely as possible.Facebook announcement is entered by Pedro Canahuati, VP Engineering, Security and Privacy.
As part of a routine security review in January, we found that some user passwords were being stored in a readable format within our internal data storage systems. This caught our attention because our login systems are designed to mask passwords using techniques that make them unreadable. We have fixed these issues and as a precaution we will be notifying everyone whose passwords we have found were stored in this way.
It would be interesting to see how many Facebook users get a notification about their plain text passwords this time.
How Facebook Claims to Protect our Passwords
In line with security best practices, Facebook masks people’s passwords when they create an account so that no one at the company can see them. In security terms, we “hash” and “salt” the passwords, including using a function called “scrypt” as well as a cryptographic key that lets us irreversibly replace your actual password with a random set of characters. With this technique, we can validate that a person is logging in with the correct password without actually having to store the password in plain text.
Because we know that people may share, reuse or have their passwords stolen, we’ve built security measures to help protect people’s accounts:
- We use a variety of signals to detect suspicious activity. For example, even if a password is entered correctly, we will treat it differently if we detect that it is being entered from an unrecognized device or from an unusual location. When we see a suspicious login attempt, we’ll ask an additional verification question to prove that the person is the real account owner.
- People can also sign up to receive alerts about unrecognized logins.
- Knowing some people reuse passwords across different services, we keep a close eye on data breach announcements from other organizations and publicly posted databases of stolen credentials. We check if stolen email and password combinations match the same credentials being used on Facebook. If we find a match, we’ll notify you next time you login and guide you through changing your password.
- To minimize the reliance on passwords, we introduced the ability to register a physical security key to your account, so the next time you log in you’ll simply tap a small hardware device that goes in the USB drive of your computer. This measure is particularly critical for high-risk users including journalists, activists, political campaigns and public figures.
Facebook Lies of Password Protection ?
Whenever I saw the message on Facebook while changing password “Your new password is too similar to your current password. Please try another password.” I wondered how Facebook can tell that a new encrypted password is similar to the old one, when everything is encrypted.
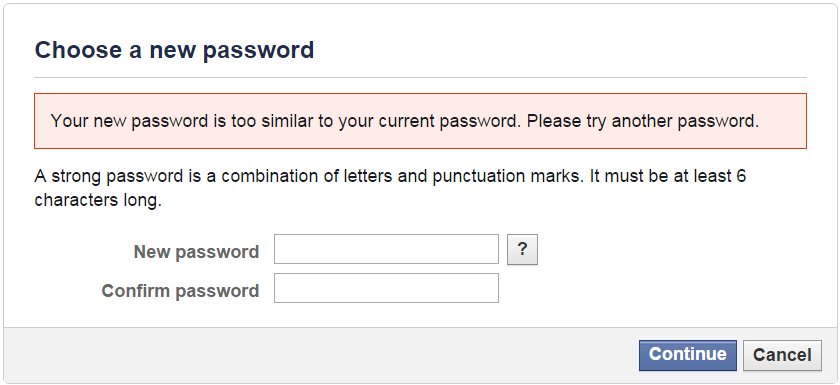

Hashed string of password would be entirely different from p@assword. The only logical explanation which I could find and other security researchers seemed to agree to it was that new user creates his Facebook account using the password: Password1. It is likely that, immediately, Facebook generates similar passwords such as: Passw0rd1. pAssword2, Passmord1 etc.
Facebook then stores their respective hashes (which are different, of course) so that if a user user types his password (after reset), the hash of the new password is compared to all these stored hashes: Facebook can tell you then if your new password is similar to the previous one or not.
This technique isn’t very plausible and not a good security practice aswell, but there is no other logical explanation. It makes one wonder Was Facebook Always storing our Passwords in Plain Text ?
Update on How Facebook Stores Password : Luca Perić on Twitter shared a Stack Exchange answer which has been vouched by Jeff Ferland who has been a moderator on StackExchange and claims to be part of the Facebook password checking process.
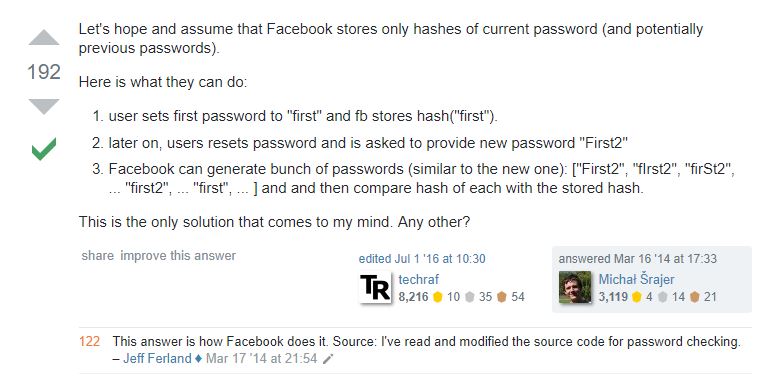

With the history and repute Facebook has in misleading users it will not come out as a surprise that they had actually stored clear text passwords. After all our passwords could enable them to shove us proper ads. What do you think about this ? Do you think Facebook might be playing nasty here aswell ? the way Cambridge Analytica Happened










Add comment