A security researcher claimed that with only $300 he intercepted terabytes of global satellite traffic including sensitive and valuable information. How this was done will be explained in this article along with the techniques used by Hackers in various Satellite Hacking.
Satellite hacking is not something new. Satellites Internet is used mostly in remote areas where cable internet does not reach but that does not mean interception can not be done in urban areas. Another good reason for its use is that it cannot be disturbed by the local government so, even after robust internet facilities these days in remote locations some people will still prefer a portable dish and decoder in their homes.
The Satellite Hacker
The security researcher goes by the name of James Pavur, a doctoral and a DPhil student at Oxford. His work is based on security of satellite systems and demonstrates the insecurities in satellite communication design.

As it was told by Pavur in how weak and insecure is the satellite security system. He bought home a television equipment worth $300 to seize terabytes of real world satellite traffic along with all the sensitive data from even some of the world’s largest organizations.
Expected Rise In The Number Of Satellites
As the world below changes with advanced technologies so does the world above in space advances as it has been claimed that from existing 2000 satellites in space the rise in number will move to 15000 satellites. The largest community of cyber security known as the information security community might make certain to improve the past security weaknesses and remove risks of leakage of censored information.
Satellite Hacking @ Black Hat
Pavur revealed in his research paper that under the proper circumstances the hijackers can hack into active sessions through satellite link.
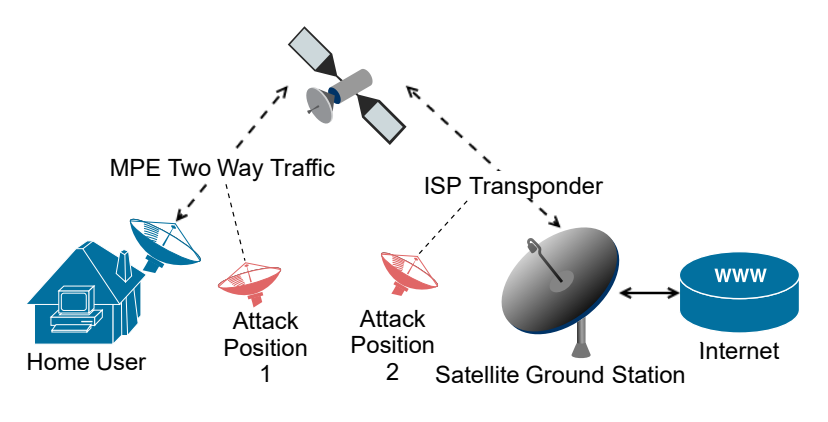
Pavur will also be presenting his brief in the upcoming Black Hat session. The briefing at Black Hat will address attacking broadband communications across 3 domains that is: land, air and sea. It will further reveal that with almost zero risk of detection these communications can be spied from thousands of miles away. Details of the attack will be disclosed in the upcoming Black Hat Conference which is scheduled in August 2020. You can check out the details about James briefing at Whispers among the Stars.
This briefing presents an experimental look at attacking satellite broadband communications. We find that an attacker using $300 of home television equipment can spy on these communications from thousands of miles away. We walk though the hardware we used and software we developed to evaluate this threat against real-world systems using two distinct communications protocols: DVB-S MPE and DVBS-2 GSE.
According to the briefing ‘Whispers among the Stars’ it is said that
From home satellite broadband customers, to wind farms, to oil tankers, to aircraft, satellite eavesdropping represents a critical threat to privacy and communications security.”
Coming down to the main part, lack of encryption in transit in large parts of data is absent. Confidentiality occurs in such a way that only the key is accessible only to the authorized users so even the minute changes can be detected.
Satellite Hacking is Decades Old
As mentioned above that satellite hacking is not new and it has been going on since the satellites started orbiting over us. One such software for starters is SkyGrabber which could easily allow you to listen to the skies.

SkyGrabber is a Russian built software which receives input from a digital satellite tuner card for hard drive recording. The same software was used to Hack American Predator Drone by Iraq back in 2008.
How Satellites Are Hacked
The list of items required to intercept satellite data stream can be easily obtained and doesn’t cost a fortune.
- A Satellite dish coupled with a bigger dish antenna, dish size should be according to the satellite you prefer, the bigger the better as size does matters. Selfsat H30D Satellite Dish or any similar device can be used.
- A PC Tuner card like TBS 6983 Satellite PCI-E
- Interception Software like SkyGrabber or PEØSAT etc
Now if you’ve gotten everything right then position your dish in accordance with your preferred satellites, start your Interception software, look for different ways to intercept down link satellite frequencies and enjoy free satellite television and be the listener of the sky. But try not to get yourself caught up in illegal activities as you can even download streams which are not intended for you.
Satellites and Encryption
It will be wrong to say that all satellites communicate in plaintext. One significant improvement since the mid-2000s has been increased adoption of SSL/TLS encryption. While this protects against certain types of eavesdropping attacks, the very process of requesting and exchanging SSL certificates leaks potentially revealing information. Pavur data included over 52,000 SSL “wildcard” certificates from around 1,200 distinct domains.
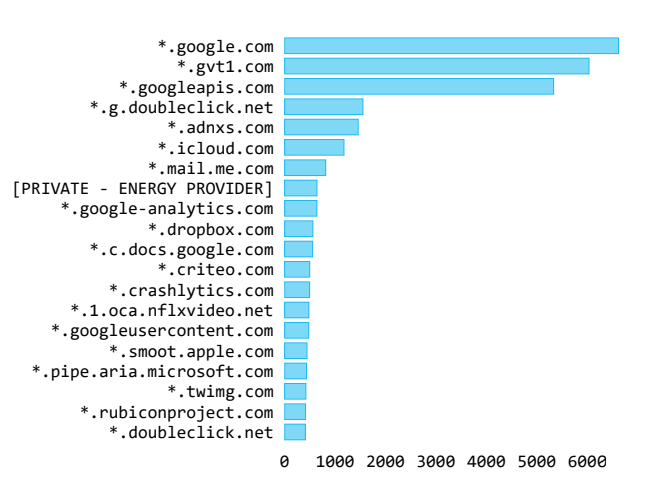

certificates. Number 8 has been hidden as it is a private subdomain range for a major energy provider.
Information a user might consider deeply private – such as TLS certificates or DNS responses from various adult websites, in fact, being broadcast across an entire continent. With collating data, such as knowledge of a user’s IP address, this risk becomes particularly severe as it violates our privacy and the fact that this can be achieved with no literal prior knowledge of cryptography makes its even more dangerous.

Types of Satellite Hacking
Satellite Hacking as already stated is not new, and has been demonstrated many a times in past aswell. Software’s like DVB Snoop and Wireshark can intercept satellite communications and gather data that hasn’t been encrypted. After setting up satellite dish pointing to the specific satellite that is broadcasting the traffic, the packets that are not encrypted will be pried on by using DVB-Snoop along with Wireshark. After identifying the IP address routed through the satellites downstream link, one can start listening for packets coming from the Internet to this specific IP. TCP hijacking attack can be easily carried out as we can view the plaintext packets now . The different satellite TCP hijacking methods are :
- Blind hijacking
- IP spoofing
- Man in the middle attack
Some of the widely used open source tools which can be used Satellite Hacking are :
- Hunt
- Shijack
- Scapy
- Juggernaut
- Other software mentioned in this write-up
Conclusion
Satellite Hacking does not mean literal taking over of satellites and deviating them from either their course or disrupting what they are meant to do. However, it is about interception of data streams, which go both ways. New Satellites may be equipped with newer tech which can enforce higher levels of encryption thus making such interception attempts futile but until the current orbiting metal is deemed obsolete we will only see increase in satellite data hacking.













Add comment