Even today, several online services ask users to submit important personal data such as their birth dates. This may be done for keeping records, for ensuring that a user is above a certain age or simply for a user’s verification. Considering that birthdays are not really “personal” or “non-public” data in today’s world, it is not a wise idea to use them for verification purposes. Yet, the practice still exists largely.


What Hackers can do from your Birth Date ?
You might think that a birth-date alone cannot be of much use to a hacker. Well, you are wrong. A single user is likely to have entered his or her birth-date on various sites. For example, a person might have entered this tiny piece of information to sign up for different newsletters, on social media sites like Facebook/ Reddit , on online video streaming websites and even on gaming hubs. All of these platforms also ask different sets of other questions. Together, this information is pretty much everything a scammer or a con-artist could ever wish for.
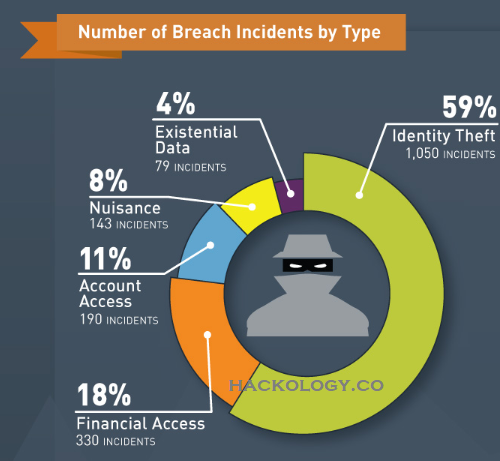

Birth Date : Start of Social Engineering
Eventually, your birth-date can be matched with your name found on different sites. A professional hacker who has access to your birth-date can easily collect more information about you (including zip code, SSN numbers and maiden’s name) from these various sites and pile them up to cause you some serious damage.
Such data can then be used to sign up for credit cards and even to apply for loans. Since birth-dates and maiden’s names are often used as security questions for account logins, a hacker could easily reset PIN codes of your valuable online accounts. Once a hacker is able to break into your account, important information about your personal or work life can further be obtained and numerous changes can be made in your data. This applies to online visa applications as well.
Hackers combine Data Points for Entry
Reveal your birth-date on site A, your relatives on site B (which gives for example mother’s maiden name), your address on site C and before you know it hackers are able to pull together a huge amount of data point which leads them to their final act “Hacking the Victim”. In all this the “birth-date” is the most important factor aswell.
That information can then be used to hack things, either directly using password reset forms, guessing passwords, etc, or indirectly through spear phishing attacks.
Another way hackers could access your computer is by sending you appropriately timed birthday greetings via e-mail. Most of you might have come across online birthday cards offered by websites such as 123greetings.com etc. If it is your birthday, make sure you only open such greetings from trusted e-mail addresses. If you end up opening a link sent by a hacker, you would be allowing the hacker to access your phone /computer device instantly. Moreover, a hacker who gets some of your valuable information (data points), may make a few calls here and there, impersonating you or someone else you know in order to get more and more details. With this, the crime is no longer just labeled as a “cyber-crime” and can get way more serious.
If any of the above seems like science fiction to you , I would suggest you better read Social Engineering: Art of Hacking and see real world examples on how hackers “do it”
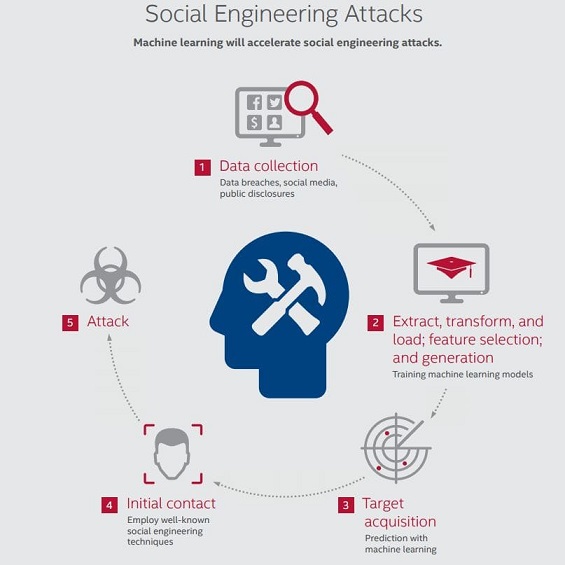

Share Less – Sweat lesser
Although there is no straight way to prevent such mishaps, it is always suggested that one should not use birth-dates in visible usernames or in passwords. Several platforms such as Yahoo do not even let a user edit the birth-date entered initially. Facebook too, allows a user to change his or her birth-date for only a limited number of times. Professionals are still trying to come up with solutions for such issues but for now, you will just have to be careful.











[…] Source link […]
[…] black market or use them to secure loans that could put your employees in debt. Even a phone number can be used as a stepping stone to finding additional private information on the […]
[…] Ref 5 & source 6 […]
[…] Cyber Awareness struck you and you have realized how little information hackers […]