Nokia Threat Intelligence Lab focuses on the behavior of malware network communications to develop detection rules that identify malware infections based on command-and-control communication and other network behavior. 

- Malware command-and-control (C2) communications
- Backdoor connections / Shells
- Attempts to infect others ( Exploits etc)
- Excessive email (Spam / Scamming )
- (Distributed) Denial of Service (DoS) and hacking activity
- Four main activities support Threat Lab signature development and verification process:
- Monitor information sources from major security vendors and maintain a database of currently active threats
- Collect malware samples (>200,000/day), classify, and correlate them against the threat database
- Execute samples matching the top threats in a sandbox environment and compare against our current signature set
- Conduct a detailed analysis of the malware’s behavior and build a new signature, if a sample fails to trigger a signature
Cyber Threat Summary
Before I move to Android and explain what all happened with Google OS, let me list down main findings of the threat report of the year as this is just the start and malware and attack vectors will only get complex as new technology evolves.
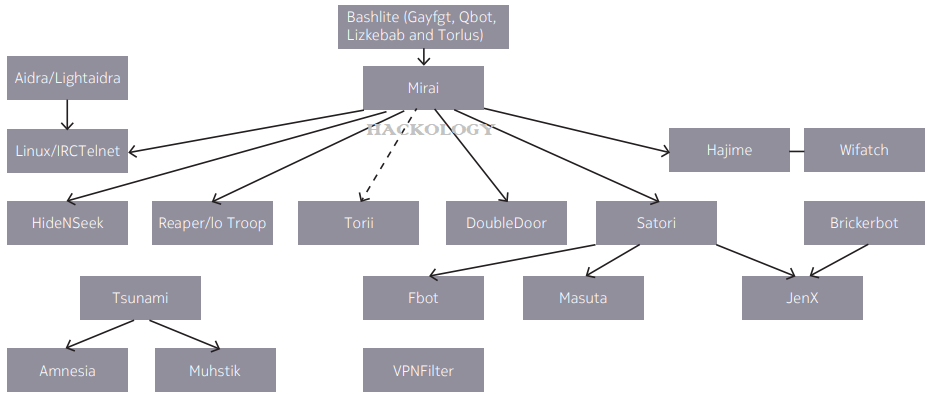
- IoT botnet activity has increased substantially since the introduction of Mirai in 2016. Many of these IoT botnets leverage the basic architecture and functionality of the Mirai source code that was released in October of that year. In 2018, IoT bot activity represented 78% of the malware network activity in carrier networks (more than double the rate seen in 2016, when IoT bot activity was first seen in meaningful numbers), with Mirai variants alone being responsible for 35%.
- IoT bots now make up 16% of the infected devices observed, up significantly from 3.5% a year ago. These bots actively scan for vulnerable victims using an increasingly rich suite of attacks. If a vulnerable IoT device is visible on the internet it will be exploited in a matter of minutes and added to a botnet.
- In networks where devices are routinely assigned public facing internet IP addresses we find a high IoT infection rate. In networks where carrier grade NAT is used, this infection rate is considerably reduced, because the vulnerable devices are not visible to network scanning.
- Malware based cryptocurrency (coin) mining has started targeting IoT devices, smartphones and even browsers which previously was limited to targeting high end servers with specialized processors
- In 2018 the average monthly infection rate in mobile networks was 0.31%. This means that in any given month, one out of every 300 mobile devices had a high threat level malware infection.
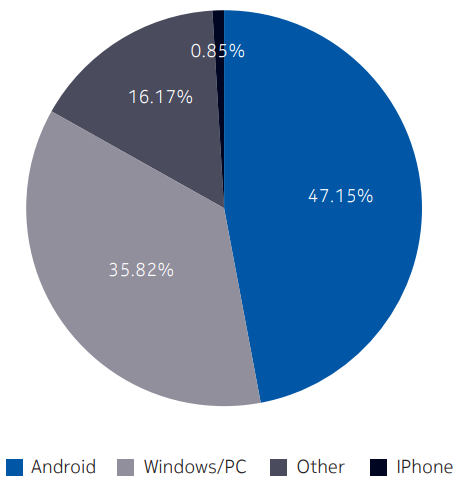
- Among smartphones, Android devices are the most commonly targeted by malware. In mobile networks, Android devices were responsible for 47.15% of the observed malware infections, Windows/PCs for 35.82%, IoT for 16.17% and iPhones for less than 1%.
- Fixed broadband networks in 2018, the average monthly infection rate per residence was 3.88%.
Android: Attackers Favorite
Among smartphones, Android devices are the most actively targeted by malware. A breakdown of infections by device type in 2017 indicates Android devices were responsible for 47.15%, Windows/PCs for 35.82%, with 16.17% on IoT devices and only 0.85% on iPhones.

Malware Growth for Android in 2018
In 2018 Android based devices are once more the main target in mobile networks
We now have close to 20 million Android malware samples. This is an increase of 31% since last year.
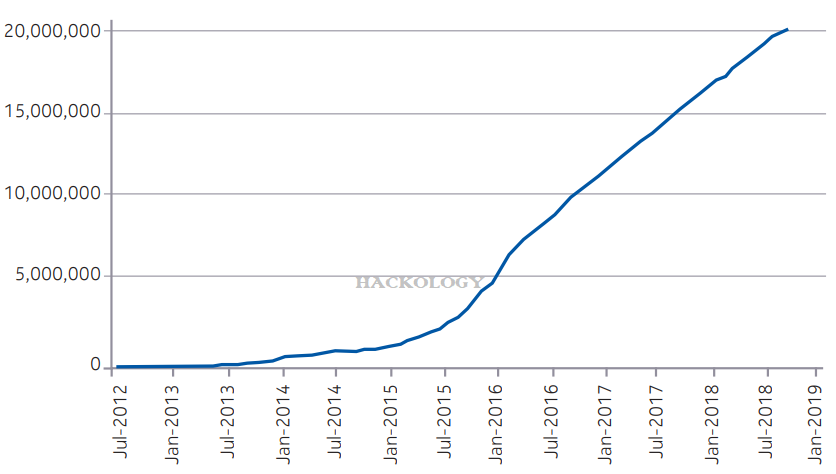

The biggest of which was the Judy malware campaign which targeted up to 36.5million Android devices with malware spread via the Google Play Store. In 2018 Android based devices are once more the main target in mobile networks. the majority of malware is now distributed as trojanized applications.
Top 20 Android Malware Threats
Android.Adware.AdultSwine
Android.Adware.Uapush.A
Android.Trojan.Leech.d
Android.Trojan.AndrClicker.D
Android.Spyware.mSpy
Android.MobileSpyware.FlexiSpy
Android.Trojan.Xgen.FH
Android.InfoStealer.Adups
Android.Trojan.Rootnik.i
Android.Trojan.Triada
Android.Trojan.Gmobi.a
Android.BankingTrojan.Marcher.A
Android.BankingTrojan.Acecard.m
Android.Trojan.HiddenApp
Android.Trojan.Sivu.C
Android.Trojan.HiddnAp.AE
Android.Worm.ADB.miner
Android.BankingTrojan.FakeCarrierMMS
Android.Trojan.Xiny.19.origin
Android.Test.FakeMalwareTomTom
Download Nokia Threat Intelligence Report 2019
You can download the report from here by filling out their form and get the report on Email , or just read it from here.
Nokia Threat Intelligence Report 2019
Conclusion
In 2018 the average percentage of devices infected each month was 0.31%. The peak month was June with 0.46% due to an increase in activity of Android.Adware.Adultswine, malware that displays ads from the web that are highly inappropriate and pornographic, attempts to trick users into installing fake “security apps” that also serve ads and entices users to register for premium services with hidden expenses. It is very persistent and difficult to uninstall.
Nokia report also stressed the emergence of new IoT botnet variants in 2018. In particular – Fbot, which is a Satori related botnet that has two major distinguishing features. It spreads by scanning for devices that have the default Android Debug Bridge (ADB) port open. Very few Androids phones have this port open, but apparently some smart TVs and other Android based IoT devices have been deployed accidentally with this debug port open.












[…] Source link […]
[…] Cyber Threats are not going to stop as technology advances, threat’s advance with them. Cyber Threat Intelligence Report 2019 shows the same analytics that even our smartphones are at risk now. A person can opt for many ways […]