Business etiquette are very important no matter which industry you are in. While chatting about Mobile Broad Band Devices used in various countries with a friend, I stumbled upon something interesting. A renowned cellular company in Pakistan ‘Zong‘ is sending its customers referral links of EasyPaisa sign-up in device inboxes.
This is not the first time, I busted Zong, few years back where they were injecting javascript in their user sessions. Let’s get into details about what I am talking about and how I have discovered the same.
Zong 4G MBB Referral Messages
If you are a user of Zong MBB internet you can check it yourself, or if you know someone who uses the same internet device you may just ask them to check it up.
- Open Zong Administrator page and login – You can access it by typing the router IP which is generally 192.168.8.1 on zong device
- Open SMS Inbox and look for messages from 3737
- You will see text something similar to this
Rs.250 are waiting for you!
Download & register Easypaisa App to get instant Rs.100. Need more? Use Easypaisa App every week to get Rs.5 daily
bit.ly/EPP100
The above message is a referral message of an EasyPaisa App sent directly by Zong
Zong Selling our MBB Numbers
MBB devices come with an ordinary cellular number but that number is not told anywhere and it can not be used be local telemarketers. Zong might say that is sent by Telenor (Parent company of EasyPaisa) but that is not the case for some reasons which I will highlight in the stripping of Referral. There are total two outcomes of how these messages come to a device where the number is not even known to its own user
- An employee of the company has sold out a list of cellular numbers and now marketing agencies are targetting those numbers. This is highly unlikely, because had that been the case we would not only be getting just referral link for only 1 service. Rather the inbox would be flooding with spam
- An employee of the company is sending these messages to users, someone who has access to sending out these messages. As the numbers are coming from someone from the inside it is very much possible that the number is spoofed to show 3737. This is highly likely as it is an affiliate ad and doable.
Stripping of Zong MBB Referral Message
The refer link used by Zong is bit.ly/EPP100 which is a shortened URL . This link was created on 15 Oct 2019 and the stats for the link show that the link has been clicked about 130,164 times which also shows that it is not one or two users it has been sent too rather to thousands.
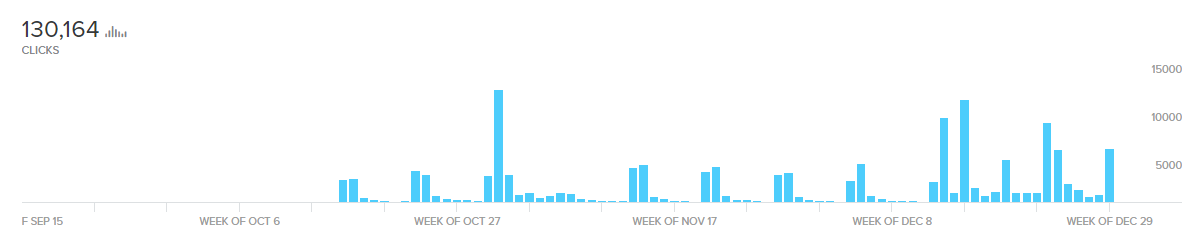

Bulk users click on this link from a “Direct Source” which mean’s majority is sent the same link in their inboxes, a search of the same referral link showed no results thus further confirming that the link is only sent to Zong MBB Users.
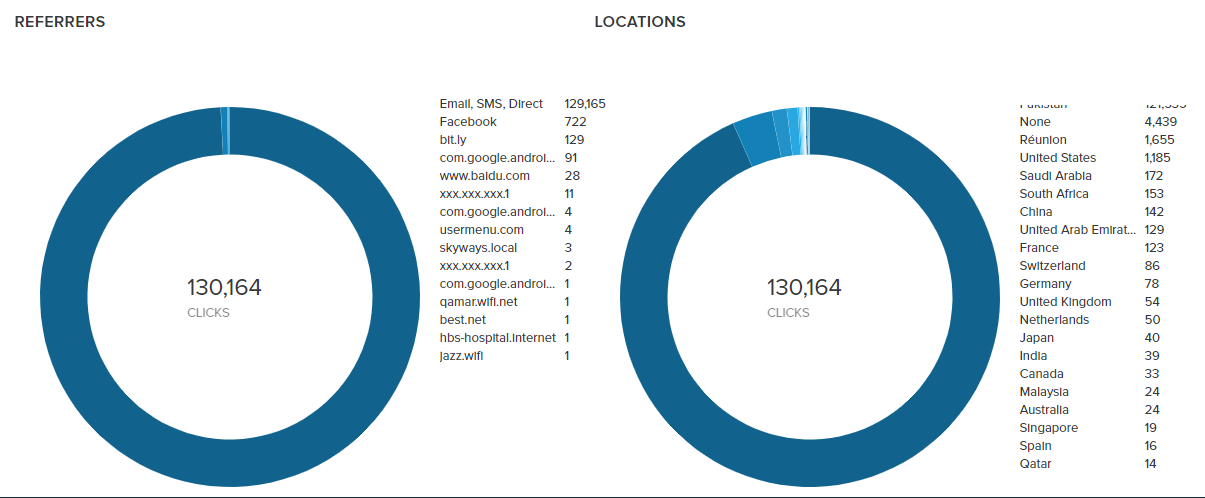

The shortened URL points to
https://easypaisa.onelink.me/cw4d/a224cb49
Which is another shortned affiliate link , where a224cd49 is an affiliate ID, opening the above mentioned link further redirects to
https://easypaisa.com.pk/?shortlink=a224cb49&pid=SMS&c=App%20Activation%20Campaign%20%28Subhan%29_15th%20Oct&af_channel=SMS&af_ad=Rs.%20100%20On%20App%20Install
The above mentioned link is little messed decode/unescape unicodes which will us
https://easypaisa.com.pk/?shortlink=a224cb49&pid=SMS&c=App Activation Campaign (Subhan)_15th Oct&af_channel=SMS&af_ad=Rs. 100 On App Install
Now the link clearly shows that this link is an App Activation Campaign made by someone named Subhan on 15th Oct , the same date when the bitly link was created and the affiliate ad is giving Rs 100 on Easypaisa App Install.
Why Afiliate links are being sent to Zong customers ? It is exploitation and making use of priviliged information, I am sure anyone can drag them in consumer court and win the appeal against them.
Ask Zong for an Explanation
The first step to do is that you should ask the company up front that why something like this is happening because you deserve to know how your data is being exploited, Use the button below to make a tweet which will tag me in the conversation aswell.
Conclusion
This also shows how user data and access is treated in Zong, User data and it’s access should be the must treasured aspect in a Cellular company and they are allowing its employees to exploit customers like this, Today it is a referral link to make some money what if tomorrow it is something more malicious ?. I do not expect Zong to understand this because they argued about far serious issues once before in past before eventually accepting their mistake. Nor that was the only copy doing shady stuff, Mobilink did something similar. No matter how many companies do such stuff it does not justify the act and is a breach and exploitation of user data privilege. I would request to highlight this issue or ask from the concerned company to explain and regulatory authorities should make strict inspection mechanism.











Same old zong tricks. Zong is overrated.